Photo illustration: Facebook vs Google (Data Security)
Facebook and Google implement advanced data security protocols, but Facebook faces more scrutiny due to frequent privacy concerns and data breaches. Discover detailed comparisons of their security measures and user privacy strategies in this article.
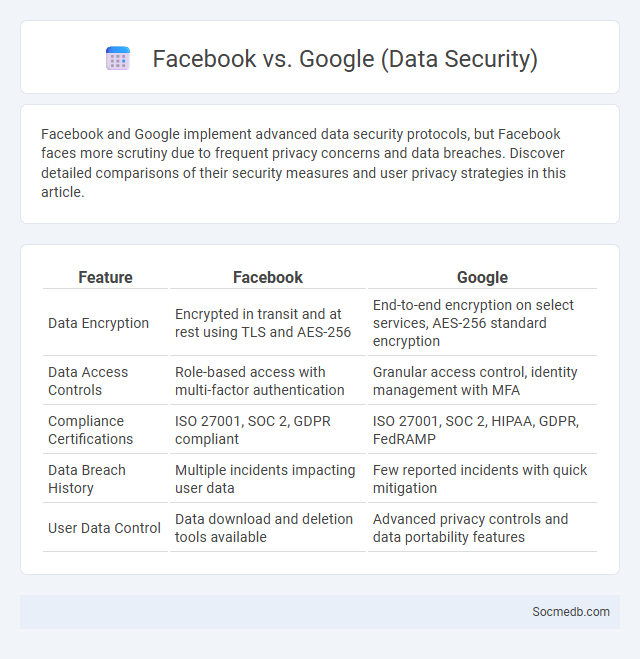
Table of Comparison
| Feature | ||
|---|---|---|
| Data Encryption | Encrypted in transit and at rest using TLS and AES-256 | End-to-end encryption on select services, AES-256 standard encryption |
| Data Access Controls | Role-based access with multi-factor authentication | Granular access control, identity management with MFA |
| Compliance Certifications | ISO 27001, SOC 2, GDPR compliant | ISO 27001, SOC 2, HIPAA, GDPR, FedRAMP |
| Data Breach History | Multiple incidents impacting user data | Few reported incidents with quick mitigation |
| User Data Control | Data download and deletion tools available | Advanced privacy controls and data portability features |
Facebook vs Google: An Overview of Data Security
Facebook and Google prioritize data security by implementing robust encryption methods and multi-factor authentication to protect user information. While Facebook focuses on safeguarding personal social interactions through continuous privacy updates and user-controlled settings, Google emphasizes comprehensive data protection across its diverse services like Gmail, YouTube, and Google Cloud with advanced AI-driven threat detection. Both companies regularly undergo third-party security audits and comply with global regulations such as GDPR and CCPA to enhance transparency and user trust.
Understanding Data Security Practices: Facebook vs Google
Facebook implements end-to-end encryption for Messenger and prioritizes user data protection through advanced threat detection systems, while Google utilizes encryption in transit and at rest, along with multi-factor authentication to safeguard user accounts. Both companies maintain comprehensive privacy policies and invest heavily in compliance with international data protection regulations such as GDPR and CCPA. Differences emerge in data handling approaches: Facebook's targeted advertising depends on extensive user profiling, whereas Google emphasizes user consent and transparency in data use across its services.
Key Differences in Data Collection Methods
Social media platforms utilize diverse data collection methods including direct user input, behavioral tracking, and third-party data integration to gather comprehensive insights. Your data is often collected through cookies, engagement metrics, and interactions within the platform, which enables personalized content delivery and targeted advertising. These methods vary significantly based on privacy policies, algorithm designs, and platform objectives, directly influencing the type and accuracy of data acquired.
How Facebook Handles User Data
Facebook processes vast amounts of user data to personalize your experience and deliver targeted advertisements. It collects information from your profile, interactions, and browsing activities, applying advanced algorithms to analyze patterns and preferences. Strict privacy policies and encryption methods are implemented by Facebook to safeguard your personal data against unauthorized access and misuse.
Google's Approach to Data Security and Privacy
Google employs advanced encryption technologies and rigorous access controls to protect your data across all social media interactions within its ecosystem. Its Privacy Sandbox initiative enhances user privacy by limiting third-party tracking while maintaining ad relevance. Continuous security audits and compliance with global data protection regulations ensure Google's commitment to safeguarding user information in social media contexts.
Major Data Breach Incidents: Facebook vs Google
Facebook experienced a major data breach in 2019 affecting over 540 million users, exposing personal information such as phone numbers and email addresses. Google faced notable security incidents, including the 2018 exposure of private data due to a software bug in Google+ that impacted over 500,000 users. Both companies have since implemented stricter data protection measures to enhance user privacy and prevent future breaches.
Response Strategies to Data Breaches
Effective response strategies to data breaches on social media involve promptly notifying affected users to maintain transparency and trust. Your company should implement robust incident response plans, including immediate containment, forensic investigation, and public communication to minimize reputational damage. Employing continuous monitoring tools and regular employee training can prevent future breaches and reinforce your data security posture.
Regulatory Compliance: GDPR, CCPA, and Beyond
Regulatory compliance in social media requires strict adherence to data protection laws like GDPR and CCPA, which govern user privacy and data handling practices. Your social media strategy must implement transparent consent mechanisms, data minimization, and rights management to avoid heavy fines and reputational damage. Staying updated with evolving regulations beyond GDPR and CCPA ensures your platform remains legally secure and trusted by users worldwide.
User Control and Data Transparency
User control over social media platforms enhances privacy by allowing individuals to customize data sharing settings and manage permissions effectively. Transparent data policies ensure users understand how their personal information is collected, stored, and utilized, fostering trust and compliance with regulations like GDPR and CCPA. Empowering users with accessible privacy dashboards and clear consent processes strengthens data security and promotes responsible digital engagement.
Future Trends: Enhancing Data Security in Big Tech
The future of social media focuses on enhancing data security through advanced encryption technologies and AI-driven threat detection systems implemented by big tech companies. Your personal information will benefit from decentralized data storage and zero-trust security frameworks that limit unauthorized access. These innovations aim to create a safer online environment while maintaining seamless user experiences across platforms.
 socmedb.com
socmedb.com