Photo illustration: Facebook vs Twitter (Data Protection)
Facebook employs advanced encryption protocols and robust user privacy controls to protect user data, whereas Twitter prioritizes transparency and rapid incident response in its data protection strategy. Explore detailed comparisons and best practices for safeguarding your information on both platforms in this article.
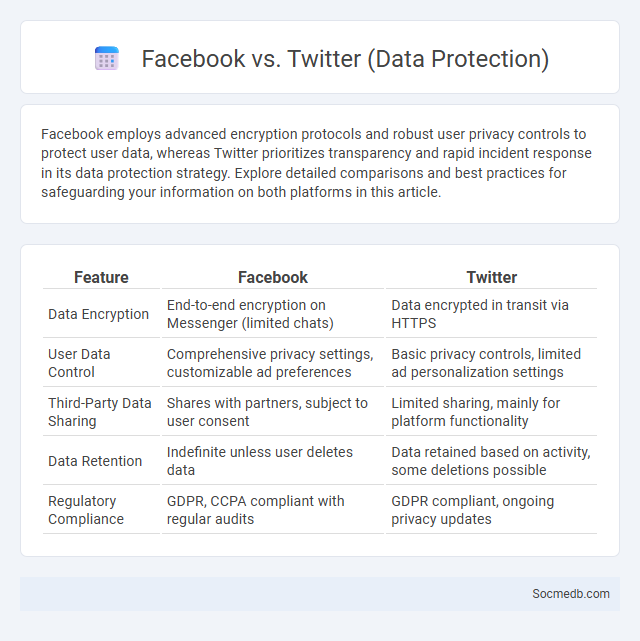
Table of Comparison
| Feature | ||
|---|---|---|
| Data Encryption | End-to-end encryption on Messenger (limited chats) | Data encrypted in transit via HTTPS |
| User Data Control | Comprehensive privacy settings, customizable ad preferences | Basic privacy controls, limited ad personalization settings |
| Third-Party Data Sharing | Shares with partners, subject to user consent | Limited sharing, mainly for platform functionality |
| Data Retention | Indefinite unless user deletes data | Data retained based on activity, some deletions possible |
| Regulatory Compliance | GDPR, CCPA compliant with regular audits | GDPR compliant, ongoing privacy updates |
Introduction: Facebook vs Twitter in Data Protection
Facebook and Twitter implement distinct data protection protocols reflecting their different social media models and user interactions. Facebook employs comprehensive privacy settings and robust encryption to safeguard personal data, emphasizing user control over shared content and targeted advertising preferences. Twitter focuses on real-time data security measures, including account verification and data access controls, to protect users from breaches and unauthorized data exploitation.
Overview of Data Protection Policies
Social media platforms implement comprehensive data protection policies designed to secure user information through encryption, access control, and regular audits. These policies ensure that Your personal data is collected transparently, stored securely, and only shared under strict compliance with regulatory frameworks such as GDPR and CCPA. Understanding these data protection measures can help You manage privacy settings effectively and safeguard Your online presence.
User Data Collection Practices
Social media platforms implement user data collection practices that track your online behavior, preferences, and interactions to deliver personalized content and targeted advertisements. These practices often involve gathering demographic information, browsing history, and location data through cookies and app permissions. Understanding how your data is collected empowers you to make informed decisions about privacy settings and data sharing preferences.
Consent Mechanisms and Transparency
Consent mechanisms on social media platforms ensure users explicitly agree to data collection practices, enhancing privacy control and regulatory compliance. Transparency is achieved through clear privacy policies, real-time notifications, and detailed explanations of data usage, fostering trust and informed decision-making. Effective implementation of these measures reduces risk of unauthorized data processing and improves user engagement by upholding ethical standards.
Security Measures and Encryption
Robust security measures and advanced encryption protocols safeguard your data on social media platforms from unauthorized access and cyber threats. End-to-end encryption ensures messages remain confidential between sender and receiver, preventing interception by third parties. Regular updates, multi-factor authentication, and secure password policies enhance the overall protection of your online presence.
Incident History: Major Data Breaches
Major data breaches in social media platforms have exposed millions of users' personal information, including names, email addresses, passwords, and private messages, leading to significant privacy concerns and identity theft risks. Platforms like Facebook, LinkedIn, and Twitter have experienced high-profile hacks, causing widespread user distrust and regulatory scrutiny. You must prioritize strong password practices and enable multi-factor authentication to protect Your social media accounts against potential breaches.
Response Strategies to Data Breach Events
Effective response strategies to social media data breach events prioritize immediate containment and transparent communication to minimize reputational damage. You should promptly identify the breach source, secure compromised accounts, and notify affected users while providing clear instructions to protect their information. Implementing ongoing monitoring and updating security protocols strengthens defenses against future data breaches on social media platforms.
Regulatory Compliance (GDPR, CCPA, etc.)
Social media platforms must adhere to regulatory compliance standards such as GDPR and CCPA, ensuring the protection of your personal data during online interactions. These regulations mandate transparent data collection, secure storage, and clear user consent protocols to prevent misuse and safeguard privacy rights. Understanding these compliance requirements helps you maintain control over your digital footprint and protects against unauthorized data exploitation.
User Trust and Platform Reputation
User trust in social media platforms is critical for fostering engagement and ensuring data privacy, directly impacting platform reputation and long-term success. Platforms with transparent policies, effective content moderation, and prompt responses to security breaches build stronger trust with Your audience. High user trust enhances platform reputation, attracting more active users and advertisers, thereby creating a sustainable digital ecosystem.
Future Trends in Social Media Data Protection
Emerging technologies like AI-driven encryption and blockchain are shaping the future trends in social media data protection, offering enhanced security and transparency. Privacy regulations such as GDPR and CCPA continue to evolve, requiring platforms to implement stricter data handling and user consent protocols. You must stay informed about these advancements to safeguard your personal information against increasingly sophisticated cyber threats.
 socmedb.com
socmedb.com