Photo illustration: doxxing vs hacking
Doxxing involves publicly revealing private personal information without consent, while hacking refers to unauthorized access to computer systems or data. Learn more about the distinct risks and protections against doxxing and hacking in this article.
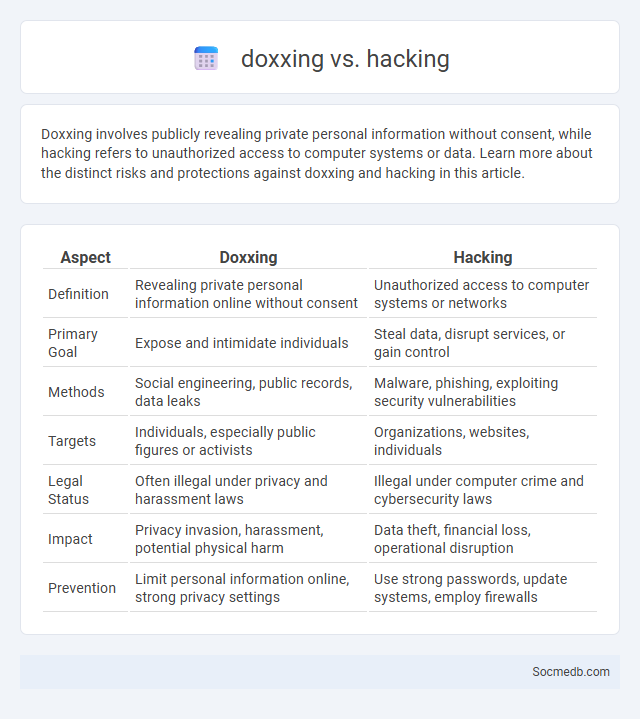
Table of Comparison
| Aspect | Doxxing | Hacking |
|---|---|---|
| Definition | Revealing private personal information online without consent | Unauthorized access to computer systems or networks |
| Primary Goal | Expose and intimidate individuals | Steal data, disrupt services, or gain control |
| Methods | Social engineering, public records, data leaks | Malware, phishing, exploiting security vulnerabilities |
| Targets | Individuals, especially public figures or activists | Organizations, websites, individuals |
| Legal Status | Often illegal under privacy and harassment laws | Illegal under computer crime and cybersecurity laws |
| Impact | Privacy invasion, harassment, potential physical harm | Data theft, financial loss, operational disruption |
| Prevention | Limit personal information online, strong privacy settings | Use strong passwords, update systems, employ firewalls |
Understanding Doxxing: Definition and Key Concepts
Doxxing involves the malicious act of publicly revealing private or identifying information about an individual without their consent, often used to intimidate or harass. Key concepts include digital privacy violations, personal data exposure such as home addresses or phone numbers, and the ethical and legal implications surrounding online harassment. Understanding doxxing is essential for enhancing cybersecurity measures and promoting responsible social media usage to protect user anonymity.
Hacking Explained: Methods and Motivations
Social media platforms face constant threats from hacking methods such as phishing, credential stuffing, and social engineering that exploit user vulnerabilities and weak passwords. Hackers are motivated by financial gain, data theft, espionage, and the desire to disrupt services or manipulate public opinion. Advanced Persistent Threats (APTs) leverage sophisticated tools to infiltrate social accounts and extract sensitive information or spread malware.
Personal Information Doxxing Unpacked
Personal information doxxing on social media involves maliciously exposing private details such as home addresses, phone numbers, and financial data to harm or intimidate individuals. This practice often leads to significant privacy breaches, identity theft, and real-world harassment, affecting users across platforms like Facebook, Twitter, and Instagram. Implementing strong privacy settings and educating users about data sharing risks are critical to mitigating doxxing incidents.
Similarities Between Doxxing and Hacking
Doxxing and hacking both involve unauthorized access to personal information, often resulting in privacy violations and potential harm to individuals. Both practices exploit vulnerabilities in digital security systems, whether through social engineering or technical breaches, to gather sensitive data. The shared intent in doxxing and hacking is to expose or manipulate private information, causing reputational damage and compromising online safety.
Key Differences Between Doxxing and Hacking
Doxxing involves publicly revealing someone's private information without their consent, often to intimidate or harass, while hacking refers to unauthorized access to digital systems or data breaches. Your online security is at risk in both cases, but the methods and targets differ significantly: doxxing exploits personal data exposure, whereas hacking exploits system vulnerabilities. Understanding these key differences empowers you to take appropriate measures to protect your digital privacy and data integrity on social media platforms.
The Unique Risks of Personal Information Doxxing
Doxxing exposes individuals to severe privacy violations by publicly revealing sensitive personal information such as home addresses, phone numbers, and financial details on social media platforms. This exposure increases the risk of identity theft, stalking, and harassment, which can lead to emotional distress and physical harm. The rapid dissemination and permanence of digital data amplify the potential consequences, making personal information doxxing a significant social media security threat.
Legal Implications: Doxxing vs Hacking
Legal implications of social media misuse vary significantly between doxxing and hacking, with doxxing involving the unauthorized release of private information often leading to civil lawsuits or criminal charges under privacy and harassment laws. Hacking constitutes illegal access to digital systems, typically prosecuted under cybersecurity statutes, resulting in severe penalties including fines and imprisonment. Both actions violate user rights and platform policies, emphasizing the importance of robust legal frameworks and enforcement to protect online privacy and security.
Real-World Examples: Doxxing, Hacking, and Personal Info Leaks
Real-world examples of social media risks include doxxing incidents where personal addresses and phone numbers are exposed, leading to harassment and safety threats. Hacking cases frequently target social media accounts to steal sensitive information or impersonate users, compromising Your online identity. Personal info leaks through platform vulnerabilities highlight the urgent need for stronger privacy settings and vigilant user practices.
How to Protect Yourself from Doxxing and Hacking
Protect your personal information by enabling two-factor authentication and using strong, unique passwords for each social media account. Regularly update your privacy settings to limit the visibility of your posts and personal details. Be cautious about sharing sensitive information online to reduce the risk of doxxing and hacking targeting your identity.
Responding to Threats: Steps After Exposure or Attack
After exposure or attack on social media, promptly assess the scope of the threat by identifying compromised accounts and unauthorized activities. Immediately change passwords and enable two-factor authentication across all affected platforms to prevent further breaches. Notify platform support teams and affected users to initiate recovery protocols and reduce potential damage from data leaks or misinformation.
 socmedb.com
socmedb.com