Photo illustration: Sockpuppet vs Clone Account
Sockpuppet accounts are fake online identities used to manipulate discussions or create false consensus, while clone accounts replicate real user profiles to deceive and impersonate individuals on social media. Learn more about identifying and protecting against these threats in this article.
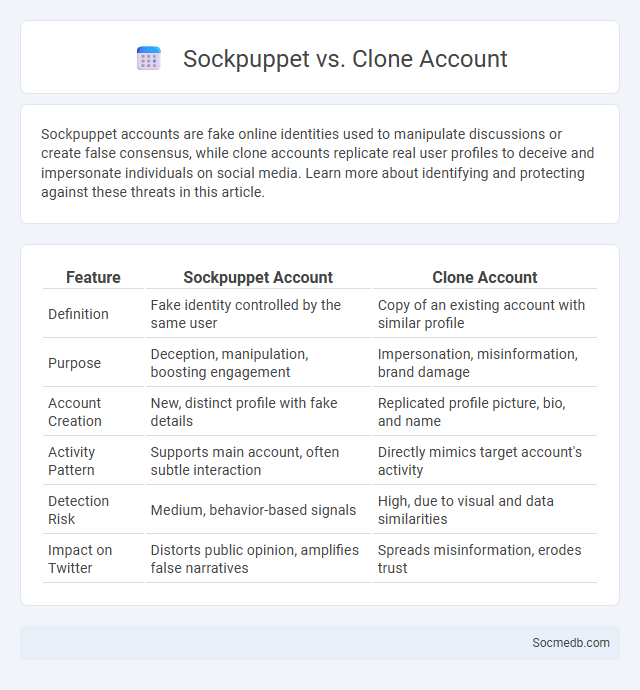
Table of Comparison
| Feature | Sockpuppet Account | Clone Account |
|---|---|---|
| Definition | Fake identity controlled by the same user | Copy of an existing account with similar profile |
| Purpose | Deception, manipulation, boosting engagement | Impersonation, misinformation, brand damage |
| Account Creation | New, distinct profile with fake details | Replicated profile picture, bio, and name |
| Activity Pattern | Supports main account, often subtle interaction | Directly mimics target account's activity |
| Detection Risk | Medium, behavior-based signals | High, due to visual and data similarities |
| Impact on Twitter | Distorts public opinion, amplifies false narratives | Spreads misinformation, erodes trust |
Introduction: Understanding Online Identity Manipulation
Online identity manipulation involves altering or fabricating personal information on social media platforms to influence perceptions and interactions. This phenomenon impacts trust, privacy, and authenticity in digital communication, affecting both individuals and organizations. Understanding these tactics helps You recognize deceptive behavior and protect Your online presence.
Defining Sockpuppet Accounts
Sockpuppet accounts are fake online identities created by individuals to manipulate social media conversations, inflate followers, or spread misinformation without revealing their true identity. These accounts often post biased opinions, impersonate others, or coordinate multiple personas to influence public perception and evade platform policies. Social media platforms employ advanced detection algorithms and user reporting mechanisms to identify and remove sockpuppet accounts to maintain digital integrity.
What Are Clone Accounts?
Clone accounts are fraudulent social media profiles created to imitate legitimate users, often mimicking their usernames, photos, and personal details to deceive followers. These accounts are commonly used for phishing, spreading misinformation, or damaging reputations by impersonating trusted individuals or brands. Detecting clone accounts involves verifying account authenticity through official badges, checking for inconsistencies in content, and monitoring for suspicious follower activity.
Key Differences Between Sockpuppet and Clone Accounts
Sockpuppet accounts involve a user creating multiple fake profiles to deceive or manipulate opinions, often to support their own views or harass others. Clone accounts replicate an existing user's profile, using identical photos and information to impersonate and potentially scam the victim's friends or followers. These account types differ mainly in intent and execution: sockpuppets are fabricated identities for covert influence, while clones are direct copies designed for impersonation and fraud.
Motivations Behind Creating Sockpuppets
Sockpuppets are created primarily to manipulate public opinion, amplify support for specific viewpoints, and shield the true identity of users in online discussions. Motivations often include promoting political agendas, evading bans or content moderation, and influencing product reviews or brand reputation. These deceptive accounts exploit anonymity to generate artificial consensus and obscure authentic interactions on social media platforms.
Common Purposes of Clone Accounts
Clone accounts on social media primarily serve to impersonate legitimate users, often aiming to deceive followers or extract personal information. These accounts are frequently used for fraudulent activities, including spreading misinformation or conducting scams. They exploit the trust associated with authentic profiles to manipulate social networks and compromise user security.
How Sockpuppets Operate in Online Spaces
Sockpuppets operate in online spaces by creating fake identities to manipulate conversations and influence public opinion, often amplifying certain narratives or misleading users. These accounts engage in coordinated behavior such as posting supportive comments, spreading disinformation, and fabricating consensus to give the appearance of widespread agreement. Platforms like Twitter and Facebook frequently detect sockpuppets through patterns in IP addresses, posting times, and linguistic similarities to combat malicious online manipulation.
Detecting and Preventing Sockpuppet and Clone Accounts
Detecting and preventing sockpuppet and clone accounts on social media involves leveraging advanced AI algorithms and machine learning techniques to analyze user behavior, posting patterns, and network connections. Platforms deploy real-time monitoring tools to identify suspicious activities such as simultaneous logins, repetitive content, and unnatural follower growth. Enhancing account verification processes with biometric authentication and multi-factor verification significantly reduces the risk of fraudulent account creation and maintains platform integrity.
Ethical and Legal Consequences
Social media platforms present significant ethical and legal consequences related to privacy violations, misinformation, and intellectual property rights infringement. Your actions on these networks must comply with data protection laws such as GDPR and avoid spreading false or copyrighted content that can lead to legal penalties. Understanding the responsibilities surrounding user data and online behavior helps prevent reputational damage and potential lawsuits.
Conclusion: Navigating Trust in Digital Communities
Navigating trust in digital communities requires vigilance and critical evaluation of information sources to protect your online reputation and privacy. Establishing authentic connections and engaging thoughtfully fosters a safer and more supportive social media environment. Prioritize transparency and consistent verification to build meaningful relationships within these digital networks.
 socmedb.com
socmedb.com