Photo illustration: Sockpuppet vs Impersonation Account
Sockpuppet accounts are fake profiles created by individuals to deceive or manipulate online discussions, while impersonation accounts mimic real users or public figures to spread misinformation or defraud others. Discover the key differences and detection methods between sockpuppetry and impersonation accounts in this article.
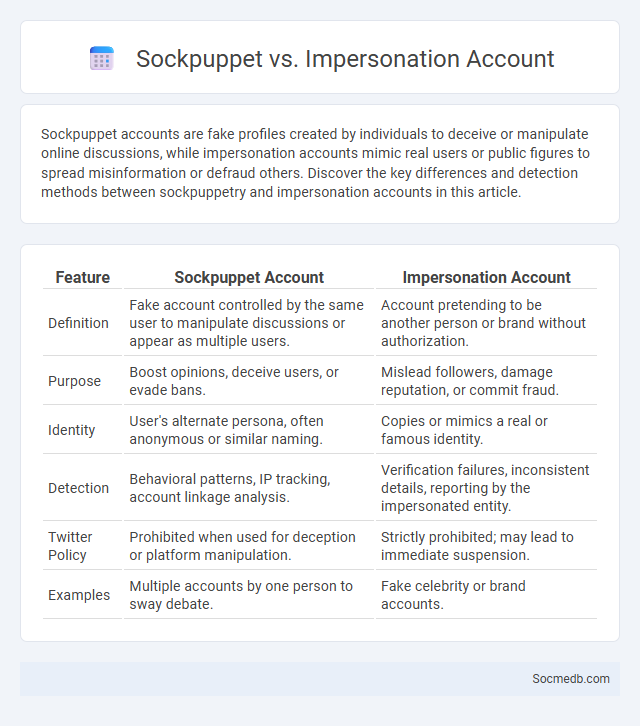
Table of Comparison
| Feature | Sockpuppet Account | Impersonation Account |
|---|---|---|
| Definition | Fake account controlled by the same user to manipulate discussions or appear as multiple users. | Account pretending to be another person or brand without authorization. |
| Purpose | Boost opinions, deceive users, or evade bans. | Mislead followers, damage reputation, or commit fraud. |
| Identity | User's alternate persona, often anonymous or similar naming. | Copies or mimics a real or famous identity. |
| Detection | Behavioral patterns, IP tracking, account linkage analysis. | Verification failures, inconsistent details, reporting by the impersonated entity. |
| Twitter Policy | Prohibited when used for deception or platform manipulation. | Strictly prohibited; may lead to immediate suspension. |
| Examples | Multiple accounts by one person to sway debate. | Fake celebrity or brand accounts. |
Understanding Sockpuppet Accounts
Sockpuppet accounts are fake online identities created to manipulate opinions, spread misinformation, or amplify certain viewpoints without revealing the true intent behind the activity. Identifying behaviors such as repetitive posting patterns, lack of personal interaction, and synchronized timing can help you detect if an account is a sockpuppet. Protecting your social media experience involves staying vigilant about these deceptive accounts that can distort authentic engagement and trust.
What Is an Impersonation Account?
An impersonation account on social media is a profile created with the intent to falsely represent another individual, typically a public figure, celebrity, or brand, often exploiting their identity for deception or fraud. These accounts can mimic personal details, images, and posts to mislead followers, damage reputations, or conduct scams, posing significant risks to both the impersonated party and the platform's community. Platforms like Facebook, Instagram, and Twitter actively implement policies and technological measures to detect and remove such accounts, protecting authentic identities and ensuring user trust.
Key Differences: Sockpuppet vs Impersonation
Sockpuppets are fake online identities created by a single person to manipulate discussions or inflate support, often used in social media marketing and political campaigns. Impersonation involves pretending to be another real individual, typically a public figure or brand, aiming to deceive followers or gain fraudulent benefits. The key difference lies in sockpuppets being wholly fabricated personas, while impersonation mimics an existing identity to mislead audiences.
Motives Behind Sockpuppetry
Sockpuppetry on social media is driven by motives such as manipulating public opinion, amplifying certain messages, and creating false consensus. It allows individuals or groups to disguise their identity, enabling them to bypass platform restrictions or avoid accountability. Understanding these motives protects your online presence from deceptive influence and promotes authentic engagement.
Why Users Create Impersonation Accounts
Users create impersonation accounts on social media primarily to mimic or deceive others by exploiting recognizable identities, often for malicious purposes such as fraud, harassment, or spreading misinformation. These accounts capitalize on the trust associated with original profiles, enabling impersonators to manipulate followers and distort online reputations. Your awareness of such tactics is crucial to protect personal information and maintain social media integrity.
Common Tactics in Sockpuppetry
Common tactics in sockpuppetry include creating multiple fake accounts to amplify messages, manipulate public opinion, and bypass platform restrictions. These accounts often engage in coordinated behaviors such as liking, sharing, and commenting to fabricate consensus. Techniques also involve using VPNs and proxy servers to hide IP addresses, making detection by social media platforms more difficult.
Detection Methods: Spotting Fake Accounts
Detection methods for spotting fake accounts on social media primarily rely on AI-driven algorithms analyzing behavioral patterns, such as posting frequency, content originality, and interaction authenticity. Machine learning models evaluate profile metadata, including account age, linked contact information, and network connections to identify anomalies. Advanced techniques incorporate image forensics and linguistic analysis to detect deepfake profiles and disingenuous language usage indicative of fake accounts.
Impact of Sockpuppets and Impersonators Online
Sockpuppets and impersonators significantly distort online social media environments by spreading misinformation and manipulating public opinion. These deceptive accounts erode trust in digital platforms, amplify fake news, and create artificial consensus, which can influence elections and consumer behavior. Detection and mitigation strategies are crucial to preserving the integrity and authenticity of online interactions.
Legal and Ethical Implications
Social media platforms raise significant legal and ethical concerns, including user privacy violations, data protection breaches, and the spread of misinformation. Compliance with regulations such as the GDPR and the CCPA is critical for companies to avoid legal penalties and maintain user trust. Ethical challenges also encompass content moderation responsibilities and balancing free speech with preventing harmful or illegal content online.
How to Report and Protect Against Fake Accounts
To report fake accounts on social media platforms, users should locate the profile's settings or help section and select the option to report impersonation or false identity. Protecting against fake accounts involves enabling privacy settings, using two-factor authentication, and regularly reviewing friend or follower lists for suspicious activity. Awareness of verified badges and being cautious with personal information shared online further minimizes risks associated with fraudulent profiles.
 socmedb.com
socmedb.com