Photo illustration: Twitter vs Bluesky ban evasion
Twitter consistently enforces strict ban evasion policies using advanced AI detection, while Bluesky's decentralized design complicates effective monitoring of ban evasion activities. Explore how these platforms tackle user restrictions and evasion tactics in this article.
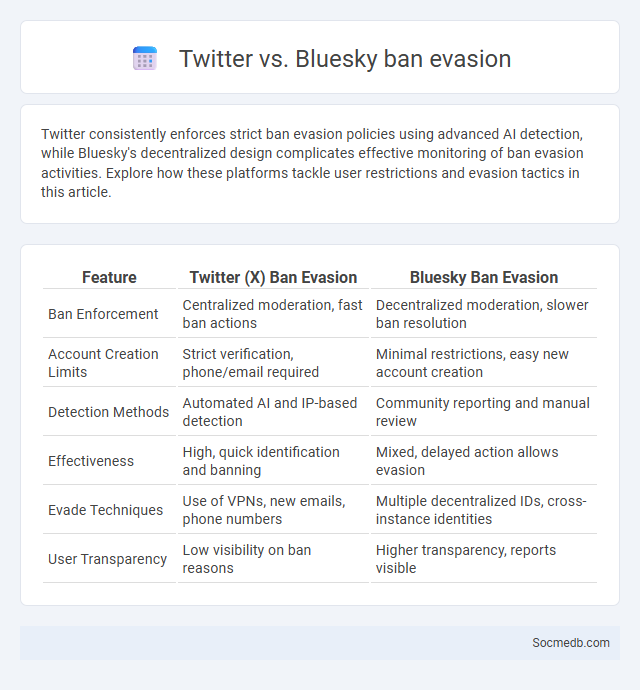
Table of Comparison
| Feature | Twitter (X) Ban Evasion | Bluesky Ban Evasion |
|---|---|---|
| Ban Enforcement | Centralized moderation, fast ban actions | Decentralized moderation, slower ban resolution |
| Account Creation Limits | Strict verification, phone/email required | Minimal restrictions, easy new account creation |
| Detection Methods | Automated AI and IP-based detection | Community reporting and manual review |
| Effectiveness | High, quick identification and banning | Mixed, delayed action allows evasion |
| Evade Techniques | Use of VPNs, new emails, phone numbers | Multiple decentralized IDs, cross-instance identities |
| User Transparency | Low visibility on ban reasons | Higher transparency, reports visible |
Introduction to Ban Evasion: Twitter vs Bluesky
Ban evasion involves users circumventing platform restrictions by creating new accounts after being banned, posing challenges for social media moderation. Twitter employs sophisticated algorithms and IP tracking to detect and prevent ban evasion, yet users still find methods to resurface. Bluesky, a decentralized platform, faces unique moderation hurdles, relying on community-driven protocols and transparency to address ban evasion while balancing user autonomy.
What is Ban Evasion?
Ban evasion refers to the act of circumventing restrictions imposed by social media platforms by creating new accounts or using alternative methods to avoid being banned. This practice attempts to bypass rules set to maintain community standards and often results in repeated violations. Understanding ban evasion helps you recognize the importance of adhering to platform policies to ensure a safe and respectful online environment.
Twitter's Approach to Ban Evasion
Twitter employs advanced machine learning algorithms and behavioral analysis to detect ban evasion by identifying accounts that attempt to circumvent suspensions through similar usernames, IP addresses, or device fingerprints. The platform's proactive enforcement includes cross-referencing activity patterns and enforcing stricter verification processes to reduce the creation of fake or duplicate accounts. These measures enhance Twitter's ability to maintain community safety and uphold platform policies effectively.
Bluesky’s Policy on Ban Evasion
Bluesky's Policy on Ban Evasion strictly prohibits creating new accounts to circumvent previous suspensions or bans, ensuring a safer and more trustworthy social media environment. Enforcement includes monitoring behaviors that indicate evasion attempts and applying account restrictions or permanent bans accordingly. Your compliance with this policy helps maintain community integrity and fosters respectful interactions across the platform.
Detection Methods: Twitter vs Bluesky
Detection methods on Twitter primarily utilize advanced machine learning algorithms and natural language processing to identify harmful content, leveraging vast datasets and user reports for real-time moderation. In contrast, Bluesky employs decentralized protocols and community-driven moderation mechanisms, emphasizing transparency and user control over content detection and removals. Both platforms aim to balance effective content moderation with user privacy, but Twitter's centralized approach allows for faster detection, whereas Bluesky prioritizes distributed trust networks.
Consequences of Ban Evasion on Both Platforms
Ban evasion on social media platforms like Facebook and Twitter undermines community guidelines and leads to increased account suspensions, reducing user trust and platform integrity. The recurrence of ban evasion often results in stricter enforcement policies and the deployment of advanced detection algorithms, which can impact legitimate users through false positives. Persistent evasion activities contribute to the spread of misinformation and harmful content, negatively affecting user experience and the platforms' reputations.
User Experiences: Evading Bans on Twitter and Bluesky
Users seeking to evade bans on Twitter and Bluesky often employ techniques such as creating multiple accounts, using VPNs to mask IP addresses, and leveraging proxy servers to bypass restrictions. These strategies impact user experiences by enabling continued platform access despite suspension, but they also raise concerns about privacy, security, and community trust. Enhanced moderation technologies and AI-driven detection systems are increasingly deployed to identify and prevent ban evasion, directly influencing user behavior and platform dynamics.
Challenges in Policing Ban Evasion
Policing ban evasion on social media presents significant challenges due to the sheer volume of content and the ability of users to create multiple anonymous accounts. Platforms must deploy advanced AI algorithms to detect and prevent banned users from circumventing restrictions, yet these tools often struggle with false positives and rapidly evolving evasion tactics. Your efforts to maintain a safe online environment depend on continuous updates to detection systems and collaboration with law enforcement agencies.
Future of Ban Evasion Prevention: Twitter and Bluesky
Twitter and Bluesky are advancing ban evasion prevention through AI-powered detection systems that analyze user behavior and network patterns in real-time. These platforms implement decentralized identity verification and encrypted authentication methods to minimize fraudulent account creation and maintain platform integrity. Future developments will likely involve enhanced machine learning algorithms and cross-platform data sharing to proactively identify and restrict ban evaders efficiently.
Conclusion: Platform Effectiveness Against Ban Evasion
Social media platforms demonstrate varying levels of effectiveness in combating ban evasion through advanced detection algorithms and user behavior analysis. Your ability to circumvent bans is increasingly limited by proactive enforcement measures and machine learning models that identify suspicious activity promptly. Continuous updates to platform policies and technology ensure stronger defenses against unauthorized account creation and content posting.
 socmedb.com
socmedb.com