Photo illustration: Twitter vs Instagram ban evasion
Twitter and Instagram face distinct challenges in ban evasion, with Twitter's open API enabling sophisticated bot networks, while Instagram's visual platform complicates detection through image-based content. Explore this article to understand the evolving tactics and preventive measures against ban evasion on both platforms.
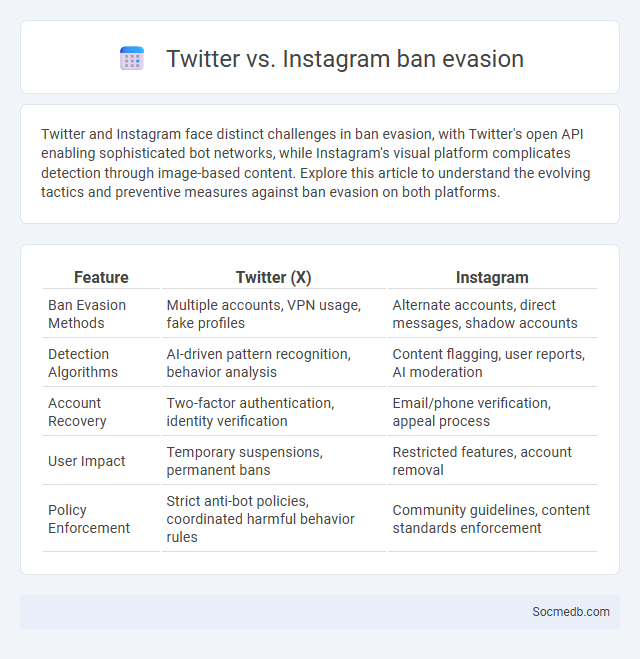
Table of Comparison
| Feature | Twitter (X) | |
|---|---|---|
| Ban Evasion Methods | Multiple accounts, VPN usage, fake profiles | Alternate accounts, direct messages, shadow accounts |
| Detection Algorithms | AI-driven pattern recognition, behavior analysis | Content flagging, user reports, AI moderation |
| Account Recovery | Two-factor authentication, identity verification | Email/phone verification, appeal process |
| User Impact | Temporary suspensions, permanent bans | Restricted features, account removal |
| Policy Enforcement | Strict anti-bot policies, coordinated harmful behavior rules | Community guidelines, content standards enforcement |
Understanding Ban Evasion: Definition and Overview
Ban evasion on social media refers to the act of circumventing platform-imposed restrictions by creating new accounts or using alternative methods to bypass account suspensions or bans. This practice undermines community guidelines and poses challenges for content moderation, leading platforms to implement advanced detection algorithms and user verification processes. Understanding ban evasion is crucial for maintaining platform integrity and ensuring a safe online environment for all users.
Twitter Ban Evasion: Common Tactics and Detection Methods
Twitter ban evasion involves users creating new accounts, using VPNs or proxy servers, and altering profile information to bypass restrictions. Detection methods include monitoring IP addresses, analyzing posting patterns, and employing machine learning algorithms to identify coordinated behavior. Your ability to recognize these tactics can help maintain platform integrity and enforce community guidelines effectively.
Instagram Ban Evasion: Techniques Users Employ
Users employ various Instagram ban evasion techniques such as creating new accounts with different emails or phone numbers, using VPN services to mask IP addresses, and avoiding flagged behavior patterns like mass following or posting restricted content. Some also exploit third-party apps designed to automate interactions while mimicking human activity to bypass Instagram's detection algorithms. These methods challenge platform enforcement by constantly evolving alongside Instagram's security updates.
Platform Policies: Twitter vs Instagram on Ban Evasion
Twitter enforces strict ban evasion policies that automatically detect and suspend accounts attempting to circumvent permanent bans using machine learning algorithms and IP address tracking. Instagram employs a combination of manual review and AI-based systems to identify and block users engaging in ban evasion by monitoring login patterns and cross-referencing device IDs. Both platforms prioritize maintaining community integrity through continuous updates to their content moderation frameworks and policy enforcement mechanisms.
Consequences of Ban Evasion on Twitter
Ban evasion on Twitter undermines platform integrity by allowing suspended users to continue spreading misinformation or harmful content, which threatens community safety. Your attempts to bypass bans can result in permanent account suspension and loss of access to valuable network connections. Twitter's enforcement measures include IP tracking and machine learning algorithms designed to detect and block evasion tactics, reinforcing consequences for users who violate policies.
Consequences of Ban Evasion on Instagram
Ban evasion on Instagram results in account suspensions, reduced reach, and potential permanent removal from the platform, negatively impacting user engagement and brand visibility. Instagram's algorithm detects repeated violations, leading to restricted features such as limited story uploads and commenting capabilities. Businesses and influencers risk losing credibility and advertising revenue due to diminished follower trust and platform penalties.
Technological Solutions: How Platforms Combat Ban Evasion
Social media platforms use advanced algorithms and machine learning techniques to identify and prevent ban evasion, ensuring banned users cannot create new accounts or bypass restrictions. Techniques such as device fingerprinting, IP tracking, and behavioral analysis help detect suspicious activities linked to previously banned accounts. Continuous updates in detection technology enable platforms to adapt to evolving evasion tactics and maintain community safety.
Ethical and Legal Implications of Ban Evasion
Ban evasion on social media raises significant ethical and legal concerns related to platform trust and user accountability. Your actions to circumvent bans can undermine community guidelines, leading to potential legal consequences such as account suspension or even prosecution under digital laws. Understanding these implications is crucial to maintaining a safe and compliant online environment.
User Experiences: Stories of Ban Evasion on Twitter and Instagram
User experiences of ban evasion on Twitter and Instagram reveal complex tactics such as creating multiple accounts, using VPNs, and altering content to bypass platform restrictions. These strategies highlight the ongoing challenges social media platforms face in enforcing policies while maintaining open communication channels. Understanding these behaviors can help you develop more effective moderation and user engagement strategies.
The Future of Ban Evasion: Evolving Strategies and Platform Responses
Ban evasion on social media is becoming increasingly sophisticated as users adopt advanced techniques like IP masking, multi-account creation, and artificial intelligence-driven behavior mimicry to bypass restrictions. Platforms are responding by enhancing machine learning algorithms, deploying biometric verification, and implementing cross-platform ban sharing to detect and prevent repeat offenders more effectively. The ongoing battle between evasive tactics and platform enforcement promises continuous evolution in digital policy and security infrastructure.
 socmedb.com
socmedb.com