Photo illustration: WhatsApp vs Threema encryption
WhatsApp uses end-to-end encryption based on the Signal Protocol, ensuring messages are secure but owned by Meta, while Threema offers decentralized, open-source encryption with no data retention, enhancing user privacy. Discover detailed comparisons of these messaging platforms and their encryption strengths in this article.
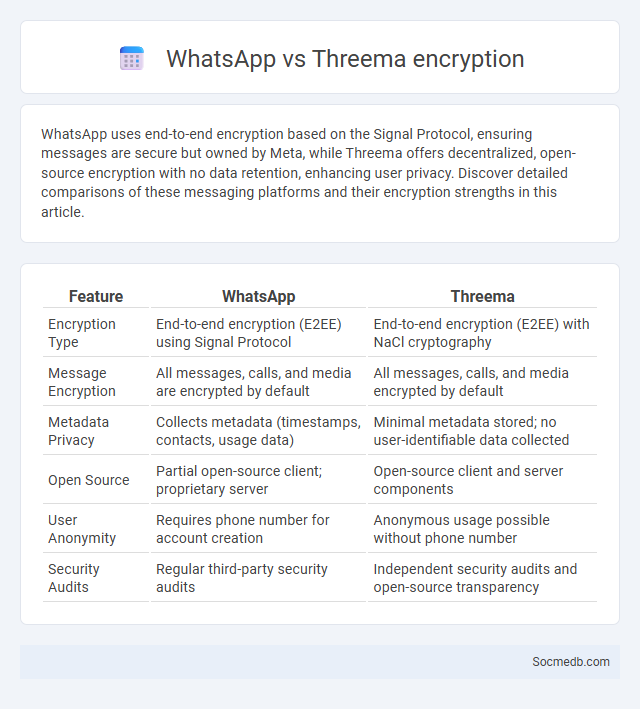
Table of Comparison
| Feature | Threema | |
|---|---|---|
| Encryption Type | End-to-end encryption (E2EE) using Signal Protocol | End-to-end encryption (E2EE) with NaCl cryptography |
| Message Encryption | All messages, calls, and media are encrypted by default | All messages, calls, and media encrypted by default |
| Metadata Privacy | Collects metadata (timestamps, contacts, usage data) | Minimal metadata stored; no user-identifiable data collected |
| Open Source | Partial open-source client; proprietary server | Open-source client and server components |
| User Anonymity | Requires phone number for account creation | Anonymous usage possible without phone number |
| Security Audits | Regular third-party security audits | Independent security audits and open-source transparency |
WhatsApp Encryption Overview
WhatsApp uses end-to-end encryption to secure all messages, calls, photos, and videos, ensuring only you and the recipient can access the content. This encryption protocol is based on the Signal Protocol, providing robust protection against third-party interceptions or unauthorized access. Your privacy is maintained by default, making WhatsApp one of the most secure messaging platforms available on social media.
Threema Encryption Overview
Threema utilizes end-to-end encryption to secure messages, ensuring that only the sender and recipient can access the content. The app employs algorithms like NaCl (Networking and Cryptography library) to provide robust security for texts, voice calls, files, and group chats. Threema's encryption also protects user metadata by routing messages through anonymous servers, enhancing privacy on social media platforms.
Understanding End-to-End Encryption
End-to-end encryption ensures that only you and the intended recipient can access the content of your social media messages, protecting your privacy from hackers and service providers. This security method encodes data at the sender's device and decodes it only at the receiver's end, making intercepted information unreadable. Understanding this technology helps you safeguard sensitive conversations across platforms like WhatsApp, Signal, and Instagram.
Encryption Protocols: WhatsApp vs Threema
WhatsApp and Threema both use end-to-end encryption protocols to secure messages, but Threema employs the NaCl (Networking and Cryptography Library) protocol while WhatsApp relies on the Signal Protocol developed by Open Whisper Systems. Threema's encryption extends to metadata protection, minimizing data exposure by not requiring a phone number or email for registration, enhancing your privacy. WhatsApp's widespread use offers robust encryption but shares limited metadata with Facebook, potentially impacting user data confidentiality.
Key Management and Security Measures
Effective key management and robust security measures are crucial for safeguarding social media accounts against unauthorized access and data breaches. Implementing multi-factor authentication, regularly rotating encryption keys, and using hardware security modules ensures your sensitive information remains protected. Organizations must also audit access controls and apply strict policies to prevent phishing attacks and data leaks on social media platforms.
User Privacy: Metadata and Content Protection
User privacy on social media platforms hinges on robust metadata management and content protection strategies to prevent unauthorized data access and misuse. Implementing end-to-end encryption and anonymizing metadata such as location, device information, and timestamps enhances security while minimizing user profiling risks. Advanced privacy controls, including customizable content visibility and encrypted messaging, empower users to safeguard their personal information effectively.
Message Delivery and Storage Security
Message delivery and storage security on social media platforms rely heavily on end-to-end encryption protocols to ensure that user communications remain confidential and protected from unauthorized access. Secure data storage employs robust cryptographic techniques and distributed databases to prevent data breaches and maintain the integrity and availability of user-generated content. Regular security audits and compliance with data protection regulations like GDPR fortify the defense mechanisms against cyber threats targeting message delivery channels.
Open Source Transparency and Audits
Open source transparency in social media platforms enhances trust by allowing independent audits of code and algorithms, ensuring data privacy and ethical content moderation. Public access to source code enables researchers and developers to identify security vulnerabilities and biases, promoting a safer user experience. Regular audits conducted by third-party organizations validate compliance with privacy regulations and contribute to accountable social media governance.
Vulnerabilities and Security Concerns
Social media platforms often face vulnerabilities such as data breaches, phishing attacks, and account hijacking that jeopardize user privacy and sensitive information. Your personal data can be exploited through weak passwords, unsecured connections, or third-party app integrations, increasing the risk of identity theft and financial fraud. Implementing strong security measures, like two-factor authentication and regular privacy settings audits, is essential to protect your social media presence from evolving cyber threats.
Choosing the Best Encrypted Messenger
When choosing the best encrypted messenger, prioritize platforms that implement end-to-end encryption protocols like Signal Protocol to ensure message confidentiality. Evaluate features such as open-source codebases, minimal metadata retention, and robust forward secrecy to enhance security and privacy. Popular options include Signal, Telegram (Secret Chats), and Threema, each offering varying degrees of encryption strength and user control.
 socmedb.com
socmedb.com