Photo illustration: YouTube spam bot vs hacking
YouTube spam bots flood comment sections with irrelevant or malicious content, while hacking targets user accounts to gain unauthorized access or control. Discover how these threats differ and how to protect yourself in this article.
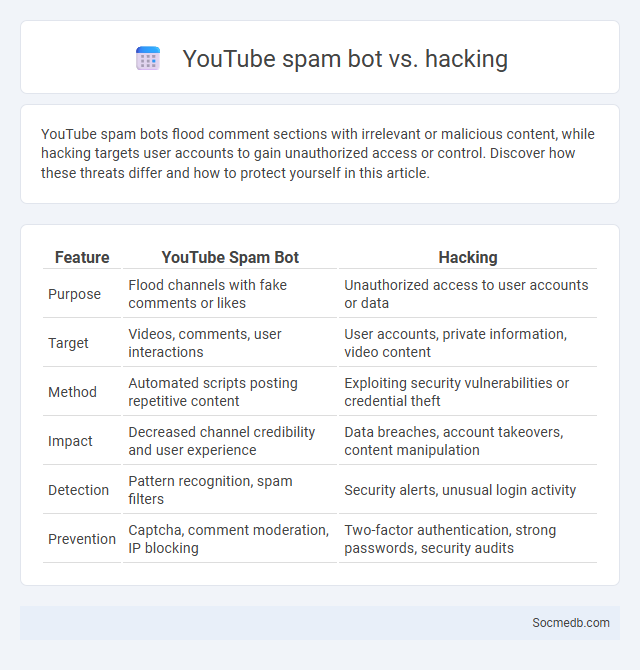
Table of Comparison
| Feature | YouTube Spam Bot | Hacking |
|---|---|---|
| Purpose | Flood channels with fake comments or likes | Unauthorized access to user accounts or data |
| Target | Videos, comments, user interactions | User accounts, private information, video content |
| Method | Automated scripts posting repetitive content | Exploiting security vulnerabilities or credential theft |
| Impact | Decreased channel credibility and user experience | Data breaches, account takeovers, content manipulation |
| Detection | Pattern recognition, spam filters | Security alerts, unusual login activity |
| Prevention | Captcha, comment moderation, IP blocking | Two-factor authentication, strong passwords, security audits |
Understanding YouTube Spam Bots: Definition and Purpose
YouTube spam bots are automated programs designed to post repetitive or irrelevant comments, likes, and subscribers to manipulate engagement metrics and disrupt community interactions. These bots often aim to promote malicious links, increase the visibility of certain channels artificially, or skew algorithmic recommendations. Your awareness of these tactics is crucial to maintaining authentic engagement and protecting your content from spam-related harm.
Common Tactics Used by YouTube Spam Bots
YouTube spam bots commonly use tactics such as posting repetitive comments filled with keywords or links to drive traffic to external websites. These bots often exploit trending videos or popular channels to maximize visibility and evade detection by frequently changing account names or using fake profiles. By mimicking human behavior through automated likes and subscriptions, spam bots manipulate YouTube's algorithm to increase the reach of spam content.
What is Hacking? Differentiating from Spam Bots
Hacking involves unauthorized access to computer systems to exploit weaknesses or steal data, often targeting social media platforms to infiltrate accounts or spread malware. In contrast, spam bots are automated programs designed to post unsolicited content, advertisements, or misleading links to disrupt social media networks and degrade user experience. Understanding the distinction is crucial for implementing effective cybersecurity measures and maintaining the integrity of online interactions.
Methods Hackers Use on YouTube Platforms
Hackers exploit YouTube platforms primarily through phishing scams embedded in video descriptions and fake channel links designed to steal personal information. They deploy malicious software via links in comments or video annotations aimed at compromising users' devices. Social engineering tactics, including fraudulent giveaways and deceptive tutorials, are frequently used to manipulate viewers into revealing sensitive data or downloading harmful software.
Spam Bots Beyond YouTube: How They Work Across Platforms
Spam bots operate across social media platforms like Instagram, Facebook, Twitter, and TikTok by automating repetitive tasks such as posting unsolicited content, sending bulk messages, and creating fake accounts to manipulate engagement metrics. These bots use sophisticated algorithms to bypass platform filters, often exploiting API vulnerabilities and mimicking human behavior to avoid detection. Understanding how spam bots infiltrate your social media presence is essential for maintaining account security and ensuring authentic interactions.
Comparing YouTube Spam Bots and General Spam Bots
YouTube spam bots specifically target video content, comments, and user subscriptions to artificially inflate engagement metrics or spread malicious links, exploiting platform algorithms differently than general spam bots, which often distribute bulk unsolicited messages via email, social media, or web forms. YouTube spam bots prioritize evading detection through mimicking human-like interaction patterns within video uploads and comments, whereas general spam bots focus on mass messaging and phishing schemes across various digital channels. The unique algorithmic environment of YouTube demands specialized bot behaviors to manipulate visibility and monetization opportunities compared to the broader tactics employed by general spam bots.
Threat Levels: YouTube Spam Bots vs. Hackers
Social media platforms face varying threat levels from YouTube spam bots and hackers, each posing distinct risks to your online presence. YouTube spam bots primarily overwhelm channels with irrelevant comments and fake likes, undermining content authenticity and damaging user trust. Hackers, however, represent a higher-level threat by potentially gaining unauthorized access to your accounts, stealing personal data, and sabotaging your digital identity.
Impact on Users: Spam Bots and Hacking Activities
Spam bots flood social media platforms with irrelevant content, undermining genuine user engagement and compromising your online experience. Hacking activities exploit vulnerabilities, leading to privacy breaches, identity theft, and unauthorized access to personal information. These threats significantly impact user trust and platform security, emphasizing the need for robust cybersecurity measures.
Detection and Prevention: Fighting Spam Bots and Hackers
Advanced algorithms and machine learning techniques are essential in the detection and prevention of spam bots and hackers on social media platforms. Real-time monitoring systems analyze user behavior patterns to identify and block malicious activities before they compromise account security. Enhanced cybersecurity measures, including multi-factor authentication and AI-driven threat intelligence, significantly reduce vulnerabilities and protect user data from cyberattacks.
Future Trends in YouTube Security: Battling Spam and Hacking
Future trends in YouTube security emphasize advanced AI-based detection systems to combat escalating spam and hacking threats. Your account protection will benefit from multi-layer authentication and real-time monitoring tools designed to identify suspicious activities instantly. Enhanced encryption protocols and machine learning algorithms will play a crucial role in maintaining platform integrity and user trust.
 socmedb.com
socmedb.com