Photo illustration: Authenticator App vs Text Message
Authenticator apps provide stronger security by generating time-based one-time passwords, reducing risks of SIM swapping and phishing attacks compared to text message verification. Explore this article to understand which method best protects your social media accounts.
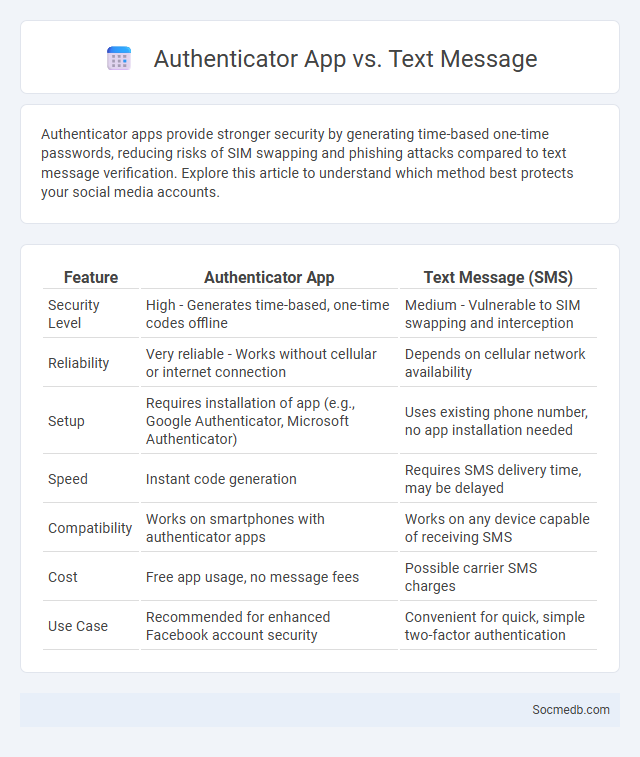
Table of Comparison
| Feature | Authenticator App | Text Message (SMS) |
|---|---|---|
| Security Level | High - Generates time-based, one-time codes offline | Medium - Vulnerable to SIM swapping and interception |
| Reliability | Very reliable - Works without cellular or internet connection | Depends on cellular network availability |
| Setup | Requires installation of app (e.g., Google Authenticator, Microsoft Authenticator) | Uses existing phone number, no app installation needed |
| Speed | Instant code generation | Requires SMS delivery time, may be delayed |
| Compatibility | Works on smartphones with authenticator apps | Works on any device capable of receiving SMS |
| Cost | Free app usage, no message fees | Possible carrier SMS charges |
| Use Case | Recommended for enhanced Facebook account security | Convenient for quick, simple two-factor authentication |
Introduction to Authentication Methods
Authentication methods in social media platforms ensure secure user access by verifying identities using techniques such as passwords, biometrics, and two-factor authentication (2FA). Strong authentication reduces unauthorized account access, protecting user data and enhancing platform trustworthiness. Advanced methods like OAuth and Single Sign-On (SSO) streamline login processes while maintaining high security standards.
What is an Authenticator App?
An authenticator app is a security tool that generates time-sensitive codes used to verify your identity during the login process on social media platforms. It enhances account protection by requiring you to enter a unique two-factor authentication (2FA) code alongside your password. This extra layer of security significantly reduces the risk of unauthorized access and keeps your social media accounts safer.
How Text Message (SMS) Authentication Works
Text message (SMS) authentication works by sending a unique, time-sensitive code directly to Your mobile phone after You enter login credentials on a website or app. This two-factor authentication method verifies Your identity by requiring the correct code, which helps prevent unauthorized access even if passwords are compromised. SMS authentication leverages the global mobile network to enhance security with minimal user effort, making it a widely adopted verification process.
Understanding Two-Factor Authentication (2FA)
Two-Factor Authentication (2FA) significantly enhances your social media account security by requiring two forms of verification: something you know (password) and something you have (a mobile device or authentication app). This extra layer mitigates risks such as phishing attacks and unauthorized access, safeguarding sensitive personal information and online interactions. Implementing 2FA on platforms like Facebook, Instagram, and Twitter ensures that your digital identity remains protected against evolving cyber threats.
Security Comparisons: Authenticator App vs Text Message
Authenticator apps provide enhanced security by generating time-sensitive, unique codes that reduce vulnerability to SIM swapping and phishing attacks. Text message (SMS) authentication relies on the cellular network, making it susceptible to interception and SIM hijacking, which compromises account safety. Users prioritizing stronger protection should opt for authenticator apps for two-factor authentication due to their reduced attack surface and increased reliability.
Usability and User Experience
Social media platforms prioritize usability and user experience by offering intuitive navigation, personalized content feeds, and seamless interaction tools that keep users engaged. Features like customizable notifications, easy-to-use sharing options, and responsive design on mobile devices enhance overall accessibility and satisfaction. Ensuring Your experience is smooth and enjoyable drives higher user retention and fosters community growth.
Vulnerabilities and Risks of Each Method
Social media platforms expose Your personal information to vulnerabilities such as data breaches, phishing attacks, and identity theft due to inadequate security measures. Risks differ across methods; for example, sharing location data increases stalking threats, while using public Wi-Fi can lead to interception of sensitive communications. Understanding these specific risks helps You protect Your privacy and avoid severe consequences like financial loss or reputational damage.
Cost and Implementation Considerations
Social media marketing expenses vary widely depending on platform choice, content creation, and advertising budgets, with small businesses often allocating 5-15% of their total marketing budget to social efforts. Implementation requires careful planning of content schedules, audience targeting, and performance analytics to maximize return on investment. Leveraging cost-effective tools such as scheduling software and analytics platforms reduces manual effort and enhances campaign efficiency.
Best Practices for Choosing an Authentication Method
Choosing the most effective authentication method enhances social media security by prioritizing multi-factor authentication (MFA), biometric verification, and secure password protocols to reduce unauthorized access. Employing encryption standards and regularly updating authentication processes ensures protection against evolving cyber threats. User-friendly interfaces combined with robust security measures significantly improve account safety and user experience on social media platforms.
Conclusion: Which Authentication Method is Right for You?
Choosing the right social media authentication method depends on your security needs, user experience preferences, and platform compatibility. Two-factor authentication (2FA) offers enhanced protection by requiring a secondary verification step, significantly reducing the risk of unauthorized access. Passwordless authentication methods, such as biometric login or magic links, provide seamless access while maintaining robust security, making them ideal for users prioritizing convenience without compromising safety.
 socmedb.com
socmedb.com