Photo illustration: Block vs Restrict
Blocking on social media prevents any interaction or visibility between users, while restricting limits how much a specific user can engage with your content without fully blocking them. Discover the key differences and best use cases for Block vs Restrict in this article.
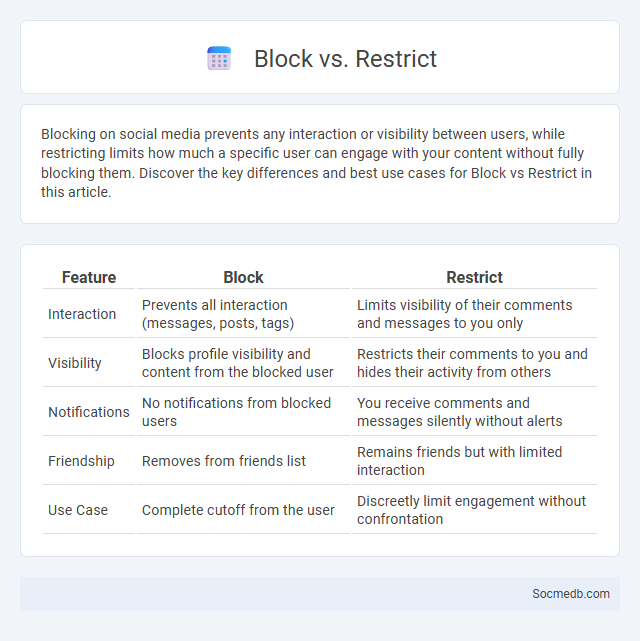
Table of Comparison
| Feature | Block | Restrict |
|---|---|---|
| Interaction | Prevents all interaction (messages, posts, tags) | Limits visibility of their comments and messages to you only |
| Visibility | Blocks profile visibility and content from the blocked user | Restricts their comments to you and hides their activity from others |
| Notifications | No notifications from blocked users | You receive comments and messages silently without alerts |
| Friendship | Removes from friends list | Remains friends but with limited interaction |
| Use Case | Complete cutoff from the user | Discreetly limit engagement without confrontation |
Understanding Block, Restrict, and Block: Key Differences
Understanding the key differences between block, restrict, and mute on social media enhances your ability to manage online interactions effectively. Blocking completely prevents a user from viewing your profile or contacting you, while restricting limits their ability to comment on your content without notifying them. Muting allows you to hide their posts and stories without cutting off communication, maintaining a subtle boundary.
What Does "Block" Mean on Social Platforms?
Blocking on social media platforms means preventing another user from interacting with you by restricting their access to your profile, posts, and messages. When someone is blocked, they cannot view your content, send friend requests, or communicate with you through direct messages. This feature enhances privacy and security by allowing users to control who can engage with their online presence.
The Functionality and Purpose of "Restrict
The "Restrict" feature on social media platforms allows users to limit interactions from specific accounts without the blocker knowing, enhancing privacy and control over their experience. It prevents restricted users from seeing when you are active or when messages are read, promoting a safer digital environment. This functionality helps manage negative interactions discreetly, supporting mental well-being and reducing online harassment.
Block vs. Restrict: When to Use Each Option
Blocking on social media completely prevents another user from viewing your profile, sending you messages, or interacting with your content, making it ideal when you want to cut off all contact due to harassment or unwanted attention. Restricting limits what the other user can see on your profile and hides their comments from others without notifying them, which is useful for managing interactions subtly and maintaining your privacy without escalating conflict. Understanding when to use block versus restrict helps you control your online experience and protect your digital space effectively.
Privacy Implications: Blocking vs. Restricting
Blocking on social media completely prevents the blocked user from viewing your profile, messaging, or interacting with your content, ensuring maximum privacy and control over your personal information. Restricting, on the other hand, limits the user's ability to see when you're active or if you've read their messages, offering a subtler layer of privacy without full severance. Understanding these distinctions helps you tailor your privacy settings to maintain your digital boundaries while managing interactions effectively.
User Experience: How Block and Restrict Affect Interactions
Block and restrict features on social media platforms significantly shape your online interactions by controlling who can view and engage with your content. Blocking users removes them entirely from your network, preventing any form of communication or content visibility, while restricting limits interaction by hiding comments and limiting message visibility without full removal. These tools enhance user experience by providing personalized control over your social environment, promoting safer and more comfortable digital interactions.
Handling Unwanted Contacts: Choosing the Right Tool
Handling unwanted contacts on social media requires selecting tools that offer privacy settings, block features, and reporting options tailored to your needs. Platforms like Facebook, Instagram, and Twitter provide customizable controls to restrict or remove unwanted interactions effectively. Ensuring you use the right combination of these tools protects your online presence and enhances your digital experience.
Limitations of Blocking and Restricting Accounts
Blocking and restricting accounts on social media platforms can reduce unwanted interactions but often fail to eliminate harassment entirely, as determined users may create alternative profiles to circumvent restrictions. Privacy settings and blocking tools are limited by platform policies and technological constraints, allowing some harmful content to persist. These measures also do not address underlying behavioral issues, highlighting the need for comprehensive moderation and user education strategies.
Reversing Block and Restrict Actions: What Happens Next?
When you reverse block or restrict actions on social media, the affected user regains the ability to view your profile, interact with your posts, and send messages based on platform guidelines. Notifications may not be sent to the user about the change, but restored access allows your mutual interactions to resume naturally. Your privacy settings and content visibility will adjust automatically to reflect the lifted restriction or block.
Best Practices for Managing Your Online Privacy
Managing your online privacy on social media involves using robust, unique passwords and enabling two-factor authentication for all accounts. Regularly updating privacy settings to restrict profile visibility and control data sharing with third-party apps helps minimize unauthorized information access. Monitoring account activity and being cautious about the personal details shared enhances protection against identity theft and cyberattacks.
 socmedb.com
socmedb.com