Photo illustration: Security Key vs Backup Codes
Security Keys provide stronger, hardware-based two-factor authentication compared to Backup Codes, which are static and can be compromised if stored insecurely. Learn more about how to maximize your social media account security in this article.
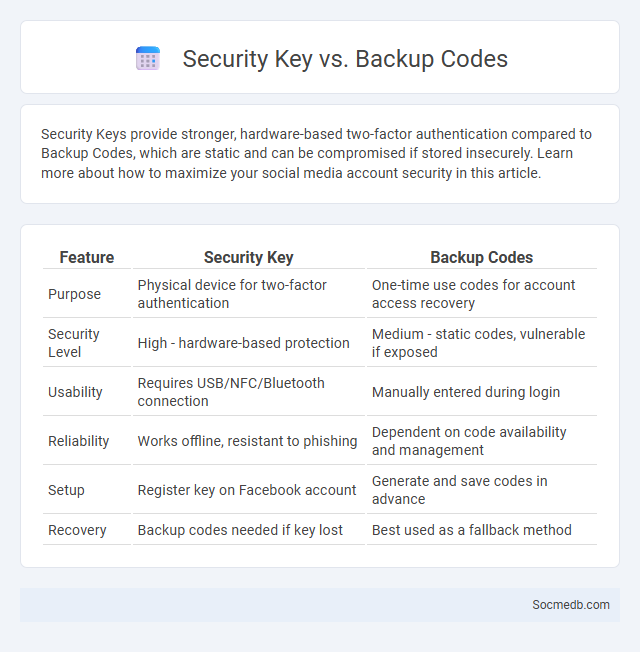
Table of Comparison
| Feature | Security Key | Backup Codes |
|---|---|---|
| Purpose | Physical device for two-factor authentication | One-time use codes for account access recovery |
| Security Level | High - hardware-based protection | Medium - static codes, vulnerable if exposed |
| Usability | Requires USB/NFC/Bluetooth connection | Manually entered during login |
| Reliability | Works offline, resistant to phishing | Dependent on code availability and management |
| Setup | Register key on Facebook account | Generate and save codes in advance |
| Recovery | Backup codes needed if key lost | Best used as a fallback method |
Introduction: Understanding Authentication Methods
Authentication methods in social media platforms are essential for ensuring user identity verification and securing accounts against unauthorized access. Techniques such as two-factor authentication (2FA), biometric verification, and single sign-on (SSO) enhance security by adding layers of protection beyond traditional passwords. Understanding these authentication protocols helps users safeguard personal information and maintain privacy across platforms like Facebook, Instagram, and Twitter.
What is a Security Key?
A security key is a physical authentication device used to enhance online account protection by providing two-factor authentication (2FA) or multi-factor authentication (MFA). It generates a unique cryptographic code that users must provide in addition to their password, significantly reducing the risk of phishing attacks and unauthorized access. Leading models include YubiKey and Google Titan, which support protocols like FIDO U2F and FIDO2 for secure social media account logins.
How Backup Codes Work
Backup codes serve as a secure secondary method to access your social media accounts when primary authentication methods, like two-factor authentication (2FA), fail or are unavailable. These codes, typically generated as a set of unique, one-time-use numbers, allow you to regain access without needing your phone or authenticator app. Storing these backup codes safely ensures your social media presence remains protected and accessible under all circumstances.
Explaining Two-Factor Authentication (2FA)
Two-Factor Authentication (2FA) enhances social media security by requiring two forms of verification before granting access to your account. Typically, after entering your password, you must provide a secondary code sent via SMS, email, or generated by an authenticator app, significantly reducing the risk of unauthorized access. Enabling 2FA on platforms like Facebook, Instagram, or Twitter strengthens your defense against hacking attempts and protects your personal information.
Security Key vs Backup Codes: Pros and Cons
Security keys provide a highly secure two-factor authentication method by using a physical device that must be present to access your social media accounts, significantly reducing the risk of phishing attacks and unauthorized access. Backup codes serve as a convenient alternative when the security key is unavailable, allowing you to regain access, but they can be compromised if not stored securely. Balancing the use of a security key with carefully managed backup codes enhances your social media security without sacrificing accessibility.
2FA vs Security Keys: Which Offers Better Protection?
Security keys provide superior protection against phishing attacks by using hardware-based authentication, making unauthorized access nearly impossible without the physical key. Two-factor authentication (2FA) enhances social media security by requiring a second verification step, but it remains vulnerable to SIM swapping and phishing if reliant on SMS codes. For optimal social media account security, hardware security keys are recommended over standard 2FA methods due to their robust resistance to remote hacking attempts.
Limitations and Risks of Backup Codes
Backup codes for social media accounts serve as essential recovery tools but carry significant limitations and risks, such as potential unauthorized access if stored insecurely or shared carelessly. Lost or compromised backup codes can result in permanent account lockout or data breaches, emphasizing the importance of secure storage methods like encrypted digital vaults or offline safekeeping. Users should regularly update and manage backup codes to mitigate risks associated with phishing attacks, device theft, and accidental deletion.
When to Use Each Authentication Method
Social media platforms employ various authentication methods such as passwords, two-factor authentication (2FA), biometric verification, and single sign-on (SSO) to balance security and user convenience. Passwords are suited for general access but are vulnerable to breaches, making 2FA essential for protecting sensitive accounts by requiring something the user knows plus a second factor like a code sent to a mobile device. Biometric authentication, including facial recognition or fingerprints, is ideal for quick, secure logins on mobile devices, while SSO enables seamless access across multiple social media accounts using one set of credentials, streamlining user experience without compromising security.
Best Practices for Enhanced Account Security
Using strong, unique passwords combined with two-factor authentication (2FA) significantly enhances your social media account security. Regularly reviewing privacy settings and revoking access for unused third-party apps minimizes vulnerabilities. Staying vigilant against phishing attempts and suspicious links protects your personal data from unauthorized access.
Conclusion: Choosing the Right Authentication Solution
Selecting the right authentication solution for social media platforms enhances user security while maintaining seamless access, crucial for preventing unauthorized account access and data breaches. Multi-factor authentication (MFA) methods, including biometric verification and time-based one-time passwords (TOTPs), provide robust protection against credential-based attacks. Balancing security level with user convenience ensures higher adoption rates, safeguarding both platform integrity and user trust.
 socmedb.com
socmedb.com