Photo illustration: SMS vs Authenticator App
SMS-based two-factor authentication is vulnerable to SIM swapping and interception, whereas authenticator apps generate time-based one-time passwords that enhance security and reduce the risk of account breaches. Discover the advantages of each method and how to choose the best option for protecting your social media accounts in this article.
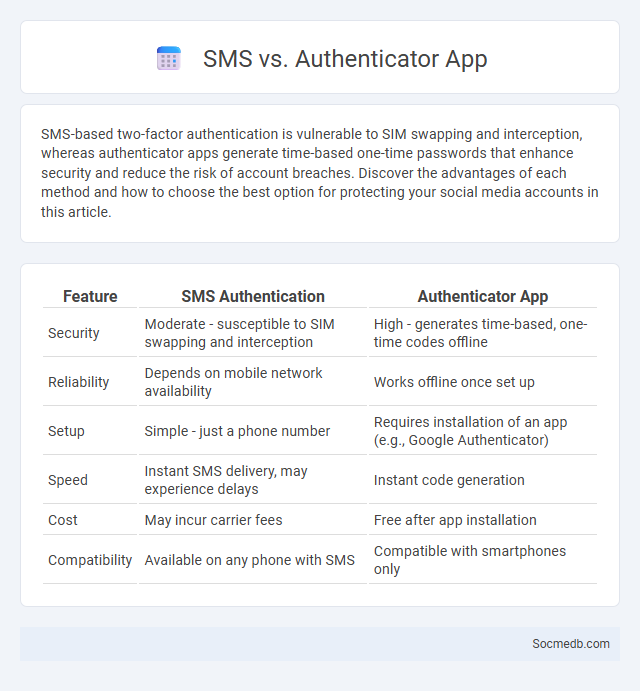
Table of Comparison
| Feature | SMS Authentication | Authenticator App |
|---|---|---|
| Security | Moderate - susceptible to SIM swapping and interception | High - generates time-based, one-time codes offline |
| Reliability | Depends on mobile network availability | Works offline once set up |
| Setup | Simple - just a phone number | Requires installation of an app (e.g., Google Authenticator) |
| Speed | Instant SMS delivery, may experience delays | Instant code generation |
| Cost | May incur carrier fees | Free after app installation |
| Compatibility | Available on any phone with SMS | Compatible with smartphones only |
Introduction to Two-Factor Authentication (2FA)
Two-Factor Authentication (2FA) enhances social media account security by requiring two forms of verification: something you know (password) and something you have (a mobile device or authentication app). This extra layer significantly reduces the risk of unauthorized access, protecting your personal information from hackers. Implementing 2FA on platforms like Instagram, Facebook, and Twitter helps safeguard your online presence against cyber threats.
What Is SMS Authentication?
SMS authentication is a security process that uses text messages to verify your identity by sending a one-time code to your mobile device. This method ensures that only authorized users can access accounts or complete transactions, enhancing protection against unauthorized access. Incorporating SMS authentication into your security measures helps safeguard sensitive information and adds a critical layer of defense against cyber threats.
How Authenticator Apps Work
Authenticator apps generate time-based one-time passwords (TOTPs) using a shared secret key and the current timestamp, ensuring secure two-factor authentication (2FA) for social media accounts. These apps synchronize with the platform's server, providing a unique, short-lived code that users must enter alongside their password to verify identity. This process significantly reduces the risk of unauthorized access by adding an extra layer of protection beyond just username and password combinations.
Security Strength: SMS vs Authenticator Apps
Authenticator apps provide stronger security than SMS by generating time-based one-time passwords (TOTPs) that are less vulnerable to interception or SIM swapping attacks. Your accounts remain safer with authenticator apps because they do not rely on cellular networks or phone numbers, reducing the risk of unauthorized access. SMS codes can be compromised through phishing and network vulnerabilities, making authenticator apps the recommended choice for enhanced account protection.
Vulnerabilities and Risks of SMS Authentication
SMS authentication exposes your accounts to vulnerabilities such as SIM swapping, where attackers hijack your phone number to intercept verification codes. The risk of SMS message interception and phishing scams further compromises security, allowing unauthorized access to sensitive information. Strengthening your security requires considering alternative multi-factor authentication methods beyond SMS to protect your digital identity effectively.
Advantages of Authenticator Apps
Authenticator apps provide a robust layer of security by generating time-based one-time passwords (TOTPs) that safeguard user accounts against unauthorized access and phishing attacks. These apps enhance account protection for platforms like Google, Facebook, and Microsoft by requiring a second verification step, ensuring that compromised passwords alone cannot grant access. Their offline functionality and ease of use further reduce reliance on SMS-based authentication, which is vulnerable to SIM swapping and interception.
User Experience and Convenience Comparison
Social media platforms prioritize user experience through intuitive interfaces and personalized content algorithms that enhance engagement and ease of navigation. Convenience is further improved by features such as seamless cross-device synchronization, instant notifications, and integrated messaging services, allowing you to stay connected effortlessly. Platforms that continuously optimize loading speeds and minimize intrusive ads provide a smoother, more satisfying social media experience.
Situational Use Cases for Each Method
Social media platforms serve different situational use cases based on their unique features and user demographics. Instagram excels in visual storytelling and brand promotion through images and short videos, making it ideal for lifestyle and fashion marketers. LinkedIn is preferred for professional networking, B2B marketing, and recruitment, while Twitter facilitates real-time news sharing and customer engagement with brief, timely updates.
Best Practices for Implementing 2FA
Implementing two-factor authentication (2FA) on social media accounts significantly enhances security by requiring an additional verification step beyond passwords. You should enable 2FA through authentication apps like Google Authenticator or Authy rather than relying solely on SMS codes, which can be vulnerable to interception. Regularly update your recovery options and periodically review connected devices to maintain control over your social media security settings.
Choosing the Right 2FA Method for Your Needs
Selecting the appropriate two-factor authentication (2FA) method is crucial for securing your social media accounts against unauthorized access. Options like authenticator apps, SMS codes, and hardware tokens vary in security and convenience, with authenticator apps such as Google Authenticator or Authy providing robust protection without relying on mobile networks. Evaluating your risk level and device compatibility ensures the chosen 2FA aligns with your security needs and usability preferences.
 socmedb.com
socmedb.com