Photo illustration: SMS vs Security Key
SMS-based authentication often faces vulnerabilities such as SIM swapping and interception, compromising account security. Security keys provide stronger, hardware-based protection for social media accounts; discover the advantages in this article.
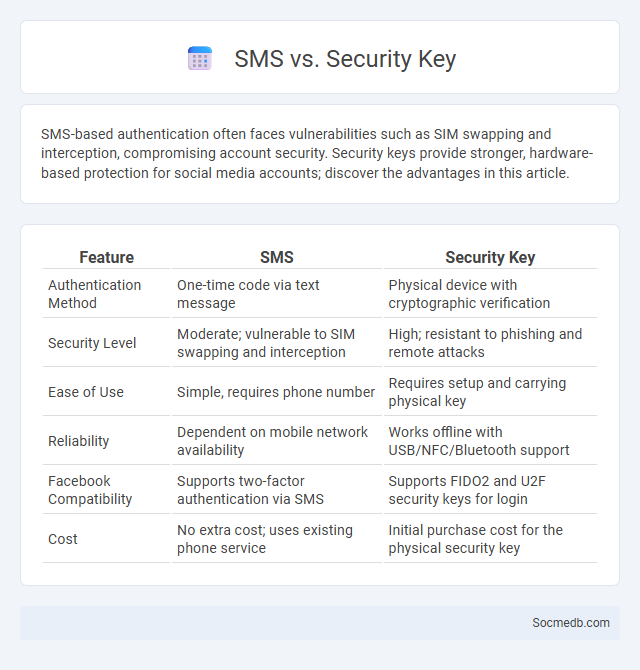
Table of Comparison
| Feature | SMS | Security Key |
|---|---|---|
| Authentication Method | One-time code via text message | Physical device with cryptographic verification |
| Security Level | Moderate; vulnerable to SIM swapping and interception | High; resistant to phishing and remote attacks |
| Ease of Use | Simple, requires phone number | Requires setup and carrying physical key |
| Reliability | Dependent on mobile network availability | Works offline with USB/NFC/Bluetooth support |
| Facebook Compatibility | Supports two-factor authentication via SMS | Supports FIDO2 and U2F security keys for login |
| Cost | No extra cost; uses existing phone service | Initial purchase cost for the physical security key |
Introduction to Authentication Methods
Authentication methods on social media platforms protect your account from unauthorized access by verifying your identity through secure processes. Common techniques include two-factor authentication (2FA), biometric verification, and password-based logins, each enhancing account security differently. Implementing robust authentication helps safeguard personal data and maintain privacy in an increasingly digital world.
What is SMS Authentication?
SMS authentication is a security process that uses text messages to verify your identity by sending a one-time code to your registered mobile number. This method enhances account protection by requiring you to enter the received code during login or transaction attempts, preventing unauthorized access. Implementing SMS authentication significantly reduces the risk of fraud by adding a layer of verification tied to your personal device.
How Security Keys Work
Security keys enhance social media account protection by using cryptographic protocols such as FIDO2 and U2F to verify user identity without relying on passwords. These physical devices generate unique, time-sensitive codes or perform cryptographic challenges during login, preventing phishing attacks and unauthorized access. By requiring the physical presence of the security key, platforms like Facebook, Twitter, and Instagram significantly reduce the risk of credential theft and account breaches.
Understanding Two-Factor Authentication (2FA)
Two-Factor Authentication (2FA) enhances social media security by requiring users to provide two forms of identification before accessing their accounts, significantly reducing the risk of unauthorized entry. Common 2FA methods include SMS codes, authentication apps like Google Authenticator, and biometric verification, each adding an extra layer of protection beyond just passwords. Implementing 2FA is crucial for safeguarding personal information and preventing account hacks on popular platforms such as Facebook, Instagram, and Twitter.
Security Comparison: SMS vs Security Key vs 2FA
Security key authentication surpasses SMS and traditional 2FA methods by providing hardware-based protection against phishing and SIM swapping attacks. SMS verification, while widely used, remains vulnerable to interception and SIM hijacking, making it the least secure option. Two-factor authentication (2FA) combining security keys or authenticator apps significantly enhances account security beyond SMS-dependent codes.
Usability and Convenience Factors
Social media platforms prioritize usability and convenience by offering intuitive interfaces, seamless navigation, and personalized content feeds tailored to Your preferences. Features such as one-click sharing, real-time notifications, and integrated messaging enhance user engagement and streamline communication. These factors contribute significantly to retaining active users and fostering continuous interaction across networks like Facebook, Instagram, and Twitter.
Vulnerabilities and Risks Associated with Each Method
Social media platforms expose Your personal data to vulnerabilities such as phishing attacks, identity theft, and data breaches that compromise account security. Risks include malware distribution through malicious links, social engineering exploits targeting user trust, and privacy invasion via oversharing or unauthorized data collection. Each method demands vigilance in managing privacy settings and recognizing suspicious activities to mitigate these threats effectively.
Best Use Cases for SMS, Security Key, and 2FA
Enhancing your social media security involves leveraging SMS-based verification, which offers a simple yet effective layer of authentication by sending one-time codes directly to your mobile device. Security keys provide the strongest protection against phishing attacks through hardware-based two-factor authentication (2FA), ensuring that only you can access your accounts. Combining SMS and security keys within a 2FA framework significantly reduces the risk of unauthorized access, safeguarding your personal data and online presence.
Cost and Implementation Considerations
Social media marketing involves costs such as content creation, advertising budgets, and analytic tools, which can vary significantly depending on platform and campaign goals. Implementation requires strategic planning, including audience targeting, consistent content scheduling, and real-time engagement monitoring to maximize ROI. Your investment in these areas directly impacts brand visibility and customer interaction effectiveness.
Choosing the Right Authentication for Your Needs
Choosing the right authentication for social media platforms is crucial to ensure user security and seamless access. Implementing multi-factor authentication (MFA) significantly reduces the risk of unauthorized access and enhances account protection. Biometric authentication, such as facial recognition or fingerprint scanning, offers a balanced approach by combining convenience with robust security measures.
 socmedb.com
socmedb.com