Photo illustration: doxxing vs public records
Doxxing involves the malicious release of private information, whereas public records contain legally accessible data about individuals. Learn how to differentiate between these sources and protect your privacy in this article.
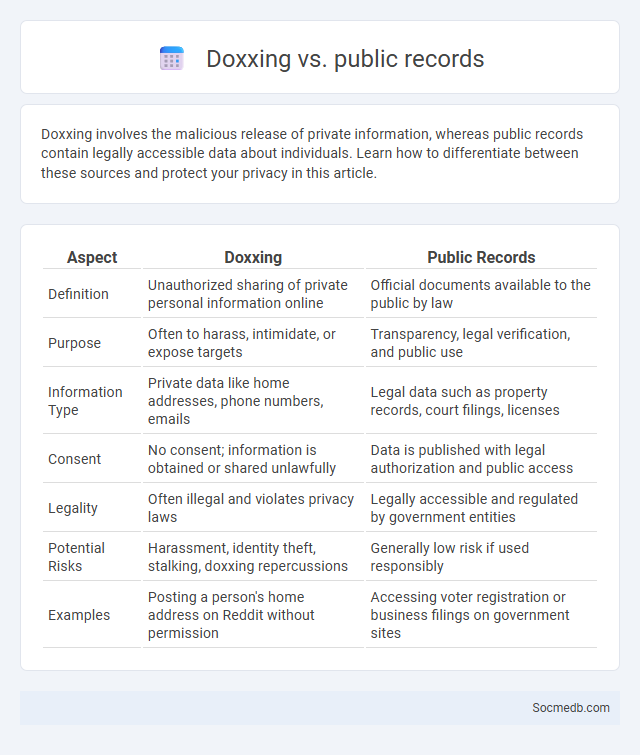
Table of Comparison
| Aspect | Doxxing | Public Records |
|---|---|---|
| Definition | Unauthorized sharing of private personal information online | Official documents available to the public by law |
| Purpose | Often to harass, intimidate, or expose targets | Transparency, legal verification, and public use |
| Information Type | Private data like home addresses, phone numbers, emails | Legal data such as property records, court filings, licenses |
| Consent | No consent; information is obtained or shared unlawfully | Data is published with legal authorization and public access |
| Legality | Often illegal and violates privacy laws | Legally accessible and regulated by government entities |
| Potential Risks | Harassment, identity theft, stalking, doxxing repercussions | Generally low risk if used responsibly |
| Examples | Posting a person's home address on Reddit without permission | Accessing voter registration or business filings on government sites |
Understanding Doxxing: Definition and Context
Doxxing involves the malicious act of publicly revealing someone's private information, such as home address, phone number, or workplace, without their consent, often leading to harassment or threats. Understanding doxxing requires recognizing its intent to intimidate or harm individuals by exploiting personal data extracted from digital footprints on social media platforms. Protecting your online presence through privacy settings and cautious sharing is essential to minimize the risk of being targeted by doxxing attacks.
What Are Public Records?
Public records are official documents or pieces of information that are maintained by government agencies and made accessible to the public. These records include data such as birth and death certificates, property deeds, court records, and marriage licenses. Social media platforms often reference or share these public records to verify identities or provide transparent background information.
Personal Information Doxxing Explained
Personal information doxxing involves the malicious act of publicly exposing someone's private details such as home address, phone number, or financial information on social media platforms without consent. This cyber harassment tactic can lead to identity theft, stalking, and severe emotional distress for victims. Protecting personal data through privacy settings and cautious sharing habits is essential to mitigate the risks associated with doxxing.
Key Differences: Doxxing vs Public Records
Doxxing involves the malicious release of private, sensitive information without consent, often leading to harassment or identity theft, whereas public records are legally accessible documents maintained by government agencies for transparency and public use. Public records include birth certificates, property deeds, and court filings, which are available through official channels, contrasting with doxxing that exploits unauthorized leaks across social media platforms. Understanding these distinctions helps users protect personal privacy while navigating information shared online.
Legal Implications of Doxxing
Doxxing on social media involves the unauthorized release of private or identifying information, which can lead to legal consequences such as lawsuits for invasion of privacy or harassment. Laws vary by jurisdiction but often include penalties under cyberstalking, defamation, and data protection regulations like the GDPR or CCPA. Platforms may also face liability issues under laws such as Section 230 of the Communications Decency Act when failing to address doxxing incidents effectively.
Privacy Risks Associated with Public Records
Public records often contain sensitive personal information that can be easily accessed and exploited on social media platforms, leading to privacy risks such as identity theft and stalking. Your data may be aggregated from various sources, increasing vulnerability to targeted scams and unauthorized use. Protecting your online presence requires vigilant management of privacy settings and regular monitoring of your information shared publicly.
How Personal Information Becomes Vulnerable
Personal information on social media becomes vulnerable through data breaches, phishing attacks, and oversharing by users. Weak privacy settings and third-party app integrations increase exposure risks, allowing cybercriminals to access sensitive details such as location, contact information, and financial data. User behavior, including accepting unknown friend requests and clicking on suspicious links, further amplifies the chances of identity theft and fraud.
Ethical Considerations in Information Sharing
Sharing information on social media demands careful attention to ethical considerations, including respecting privacy rights and avoiding the dissemination of misinformation or harmful content. You should verify the accuracy of sources and consider the potential impact of your posts on individuals and communities to promote responsible communication. Upholding transparency and consent in data sharing fosters trust and accountability in digital interactions.
Protecting Yourself from Doxxing
To protect yourself from doxxing on social media, use strong privacy settings to limit the visibility of your personal information and avoid sharing sensitive details publicly. Regularly audit your online presence to identify and remove any potentially harmful data that could be exploited. You should also enable two-factor authentication to enhance account security and be cautious about accepting connection requests from unknown users.
Best Practices for Safeguarding Personal Data
To safeguard personal data on social media, users should regularly update privacy settings to limit data exposure and avoid sharing sensitive information publicly. Utilizing strong, unique passwords combined with two-factor authentication enhances account security against unauthorized access. Monitoring account activity and being cautious of suspicious links or friend requests further reduces the risk of data breaches and identity theft.
 socmedb.com
socmedb.com