Photo illustration: Twitter vs Threads ban evasion
Twitter rigorously enforces bans, using AI and manual reviews to detect and block ban evasion attempts, while Threads currently employs less stringent measures, allowing some users to circumvent restrictions. Explore this article to understand the evolving strategies platforms use to combat ban evasion.
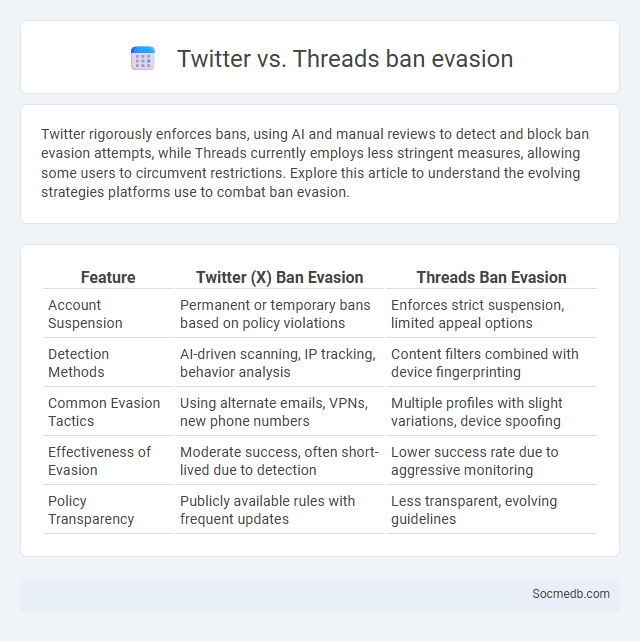
Table of Comparison
| Feature | Twitter (X) Ban Evasion | Threads Ban Evasion |
|---|---|---|
| Account Suspension | Permanent or temporary bans based on policy violations | Enforces strict suspension, limited appeal options |
| Detection Methods | AI-driven scanning, IP tracking, behavior analysis | Content filters combined with device fingerprinting |
| Common Evasion Tactics | Using alternate emails, VPNs, new phone numbers | Multiple profiles with slight variations, device spoofing |
| Effectiveness of Evasion | Moderate success, often short-lived due to detection | Lower success rate due to aggressive monitoring |
| Policy Transparency | Publicly available rules with frequent updates | Less transparent, evolving guidelines |
Understanding Ban Evasion: Definition and Implications
Ban evasion on social media refers to the deliberate act of circumventing platform-imposed restrictions by creating new accounts or using alternate identities after being banned. This behavior compromises community safety, undermines enforcement policies, and poses challenges for content moderation algorithms. Understanding ban evasion helps you recognize the risks it poses to digital trust and platform integrity.
Twitter’s Policy on Ban Evasion: An Overview
Twitter's Policy on Ban Evasion strictly prohibits users from creating new accounts to circumvent permanent suspension or restrictions, ensuring enforcement consistency across the platform. The policy uses automated detection systems combined with manual review to identify and remove accounts involved in ban evasion, safeguarding community integrity. Violations may result in immediate account suspension, reflecting Twitter's commitment to preventing abuse and maintaining a safe user environment.
Threads’ Approach to Monitoring Ban Evasion
Threads employs advanced AI algorithms and machine learning techniques to detect patterns indicative of ban evasion, enhancing platform integrity. The platform analyzes account behavior, IP addresses, and interaction networks to identify and suspend duplicate or fraudulent accounts swiftly. Continuous monitoring coupled with user reporting mechanisms ensures that ban evasion is minimized, promoting a safer and more authentic social media environment.
Key Differences in Enforcement: Twitter vs Threads
Twitter enforces content policies through a combination of automated detection and human review, often imposing stricter rules on misinformation, hate speech, and harassment with transparent public appeals processes. Threads employs a more community-driven moderation approach, relying heavily on user reports and in-app prompts to manage inappropriate content, resulting in faster but sometimes less consistent enforcement. The distinction in enforcement methodologies impacts user experience, with Twitter prioritizing comprehensive policy adherence and Threads emphasizing real-time, peer-regulated content control.
Detection Methods: How Platforms Identify Ban Evasion
Social media platforms employ advanced detection methods such as machine learning algorithms and behavioral analysis to identify ban evasion by tracking IP addresses, device fingerprints, and user activity patterns. These platforms utilize natural language processing to detect disguised content and monitor account associations to flag coordinated evasion attempts. Continuous data monitoring combined with cross-platform collaboration enhances the accuracy of identifying users circumventing bans.
User Behavior: Strategies Employed for Ban Evasion
Users employ sophisticated techniques such as leveraging VPNs and proxy servers to mask IP addresses and circumvent social media bans. Alternative accounts and alias creation further facilitate access to restricted platforms, often coupled with automated tools like bots to replicate human activity and avoid detection. Behavioral pattern analysis by social media algorithms targets these evasion strategies, leading to continuous adaptation among users to maintain platform access.
Consequences of Ban Evasion on Twitter and Threads
Ban evasion on Twitter and Threads often leads to account suspension, loss of follower trust, and reduced platform credibility. Users attempting to bypass restrictions frequently face stricter enforcement algorithms and prolonged bans, undermining community guidelines. Persistent evasion disrupts user experience and can result in permanent removal from the social media ecosystem.
Legal and Ethical Considerations in Ban Enforcement
Ban enforcement on social media platforms requires strict adherence to legal frameworks like the GDPR and COPPA to protect users' privacy rights. Ethical considerations involve ensuring transparency in content moderation policies and avoiding biased or discriminatory practices against specific groups. You must understand these principles to navigate social media regulations responsibly and uphold user trust.
Effectiveness of Ban Evasion Prevention Tools
Ban evasion prevention tools enhance social media platform security by detecting and blocking repeat offenders who create new accounts to bypass restrictions. Advanced algorithms analyze user behavior patterns and IP addresses to identify suspicious activities, significantly reducing harmful content circulation. Continuous improvements in machine learning models increase the accuracy of these tools, ensuring safer online communities and compliance with platform policies.
Future Trends: Evolving Tactics Against Ban Evasion
Social media platforms are deploying advanced AI algorithms and machine learning models to detect and counteract ban evasion tactics, including the creation of fake accounts and coordinated inauthentic behavior. You must stay informed about emerging technologies like biometric verification and decentralized identity systems that enhance user authentication and reduce anonymity exploited for evasion. Predictive analytics and real-time monitoring tools are increasingly critical in adapting policies to evolving threats, ensuring safer and more transparent online interactions.
 socmedb.com
socmedb.com