Photo illustration: WhatsApp Two-step verification vs Google Authenticator
WhatsApp Two-step verification enhances account security by requiring a PIN along with your phone, while Google Authenticator generates time-based one-time passwords for multiple apps, offering broader protection. Discover the key differences in security and usability between these verification methods in this article.
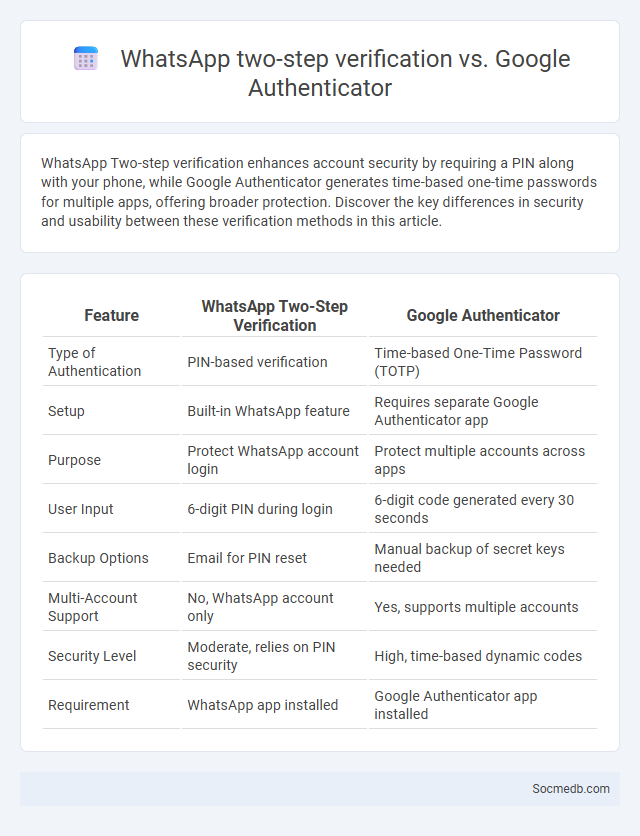
Table of Comparison
| Feature | WhatsApp Two-Step Verification | Google Authenticator |
|---|---|---|
| Type of Authentication | PIN-based verification | Time-based One-Time Password (TOTP) |
| Setup | Built-in WhatsApp feature | Requires separate Google Authenticator app |
| Purpose | Protect WhatsApp account login | Protect multiple accounts across apps |
| User Input | 6-digit PIN during login | 6-digit code generated every 30 seconds |
| Backup Options | Email for PIN reset | Manual backup of secret keys needed |
| Multi-Account Support | No, WhatsApp account only | Yes, supports multiple accounts |
| Security Level | Moderate, relies on PIN security | High, time-based dynamic codes |
| Requirement | WhatsApp app installed | Google Authenticator app installed |
Introduction to Two-Step Verification
Two-step verification enhances social media account security by requiring users to provide two forms of identification before access is granted. This process typically involves entering a password followed by a code sent via SMS, email, or authentication apps. Implementing two-step verification significantly reduces the risk of unauthorized access and protects personal information from cyber threats.
Overview of WhatsApp Two-Step Verification
WhatsApp Two-Step Verification enhances your account security by requiring a six-digit PIN when registering your phone number with the app again. This added layer protects against unauthorized access, even if someone acquires your SIM card or verification code. Enabling this feature helps safeguard your personal messages and data from potential cyber threats on social media platforms.
Understanding Google Authenticator
Google Authenticator enhances your social media security by generating time-based one-time passwords (TOTPs) for two-factor authentication (2FA). It synchronizes with your social media accounts, providing an extra layer of protection beyond your password. Using Google Authenticator helps safeguard your personal data and prevents unauthorized access to your online profiles.
How Generic Two-Step Verification Works
Generic two-step verification enhances your social media security by requiring two forms of identification before granting access. First, you enter your password, then you provide a secondary code sent via SMS, email, or generated by an authentication app. This layered authentication process significantly reduces the risk of unauthorized access to your accounts.
Security Features Comparison
Social media platforms prioritize user security through various features such as two-factor authentication, end-to-end encryption, and advanced privacy settings. Facebook and Instagram offer comprehensive security tools including login alerts and account recovery options, while Twitter emphasizes real-time monitoring to prevent unauthorized access. LinkedIn integrates secure communication protocols and privacy controls tailored for professional networking, highlighting the importance of safeguarding sensitive information across diverse social networks.
Ease of Use and User Experience
Social media platforms prioritize intuitive interfaces with streamlined navigation, enabling users to effortlessly create, share, and engage with content. Features such as customizable feeds, real-time notifications, and integrated multimedia tools enhance user experience by catering to individual preferences and reducing friction. Consistent updates and user-centric design principles ensure accessibility across devices, fostering sustained interaction and satisfaction.
Platform Compatibility and Accessibility
Social media platforms ensure broad platform compatibility by supporting various operating systems such as iOS, Android, and Windows, enabling seamless user experiences across smartphones, tablets, and desktop devices. Accessibility features like screen readers, voice commands, and customizable text sizes cater to users with disabilities, enhancing inclusivity and user engagement. Responsive design and regular updates maintain functionality and performance consistency across diverse devices and network conditions.
Recovery and Backup Options
Social media platforms offer robust recovery and backup options to protect user data from accidental deletion or cyber threats. Features such as cloud-based backups, activity logs, and multi-factor authentication enhance data security and allow seamless restoration of accounts. Users benefit from automated data export tools and platform-specific recovery protocols designed to minimize data loss and ensure continuous access.
Pros and Cons of Each Method
Social media platforms offer diverse methods like posts, stories, and live videos, each with unique advantages and drawbacks. Posts provide lasting content and enhance SEO but often require consistent quality to maintain engagement, while stories offer ephemeral, real-time interaction that boosts immediacy but lack long-term visibility. Live videos generate authentic audience connection and immediate feedback but demand careful planning and can suffer from technical issues impacting user experience.
Choosing the Best Two-Step Verification Solution
Selecting the best two-step verification solution for social media involves prioritizing methods that combine strong security with user convenience, such as authenticator apps, hardware tokens, or SMS codes. Authenticator apps like Google Authenticator or Authy provide robust, time-based one-time passwords (TOTP) that reduce the risk of phishing and SIM swapping attacks. Hardware tokens like YubiKey offer the highest level of protection by requiring physical access, making them ideal for users seeking advanced security measures on platforms like Facebook, Instagram, and Twitter.
 socmedb.com
socmedb.com