Photo illustration: Activity Log vs Privacy Shortcuts
Activity Log provides a detailed record of your interactions and posts on social media, enabling you to review and manage your digital footprint. Privacy Shortcuts offer quick access to control settings, allowing you to adjust who can see your content and manage data preferences efficiently; discover more about optimizing your social media privacy in this article.
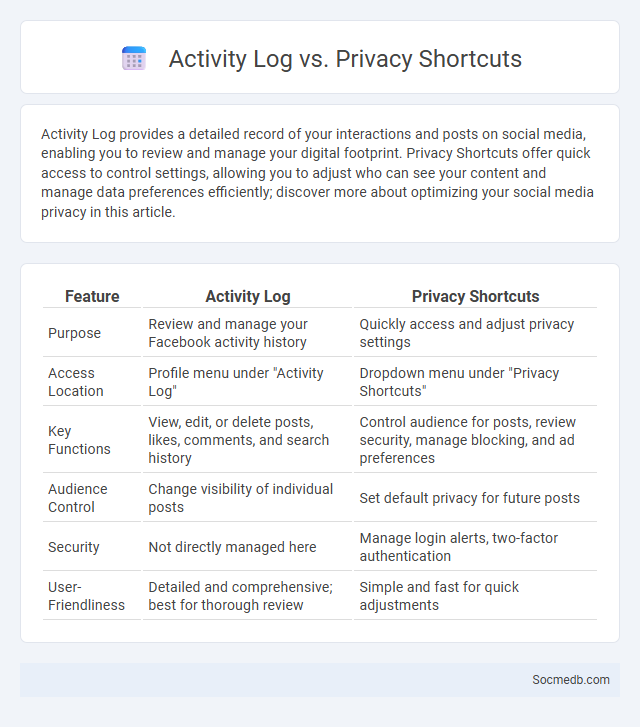
Table of Comparison
| Feature | Activity Log | Privacy Shortcuts |
|---|---|---|
| Purpose | Review and manage your Facebook activity history | Quickly access and adjust privacy settings |
| Access Location | Profile menu under "Activity Log" | Dropdown menu under "Privacy Shortcuts" |
| Key Functions | View, edit, or delete posts, likes, comments, and search history | Control audience for posts, review security, manage blocking, and ad preferences |
| Audience Control | Change visibility of individual posts | Set default privacy for future posts |
| Security | Not directly managed here | Manage login alerts, two-factor authentication |
| User-Friendliness | Detailed and comprehensive; best for thorough review | Simple and fast for quick adjustments |
Understanding Activity Log: Detailed Overview
The Activity Log on social media platforms provides a comprehensive record of all user interactions, including likes, comments, shares, and posts, enabling precise tracking of digital footprints. This feature helps users manage their privacy settings by reviewing and deleting specific activities to control what information is visible to others. Detailed analytics within the Activity Log offer valuable insights into engagement patterns, informing more strategic content creation and audience targeting.
What Are Privacy Shortcuts?
Privacy shortcuts on social media platforms are quick access tools that allow users to manage their account's privacy settings efficiently. These shortcuts enable control over who can see posts, personal information, and activity status, enhancing user security without navigating complex menus. By providing a centralized hub for adjusting visibility options, privacy shortcuts help users protect their data and maintain online confidentiality.
Exploring Privacy Settings: Key Features
Social media platforms offer a range of privacy settings that control who can view Your posts, send messages, and access profile information. Key features include customizable audience selection, activity visibility controls, and options to manage third-party app permissions. Understanding and adjusting these settings ensures Your online interactions remain secure and tailored to Your comfort level.
Activity Log vs Privacy Shortcuts: Core Differences
The Activity Log records all user interactions on social media platforms, providing a comprehensive timeline of posts, comments, likes, and shares for easy review and management. Privacy Shortcuts offer quick access to customizable security settings, enabling users to control who can see their content, manage blocked users, and adjust data sharing preferences. While the Activity Log emphasizes transparency and content visibility, Privacy Shortcuts focus on user control and protection of personal information within the social media environment.
Activity Log vs Privacy Settings: Control Comparison
Activity Log records every interaction on social media platforms, providing a detailed history of likes, comments, shares, and posts for user review and management. Privacy Settings allow users to control who can view their profile, posts, and personal information, enabling customization of access levels such as public, friends, or private. Comparing the two, Activity Log offers transparency by tracking actions, while Privacy Settings empower users to proactively restrict visibility and protect their data.
Privacy Shortcuts vs Privacy Settings: User Accessibility
Privacy Shortcuts offer a streamlined interface that allows you to quickly control who can see your posts, manage blocked users, and customize ad preferences with just a few taps, enhancing user accessibility. In contrast, Privacy Settings provide a more detailed and comprehensive range of controls, often requiring deeper navigation and understanding, which may be challenging for less tech-savvy users. Prioritizing Privacy Shortcuts improves immediate control over your online presence without sacrificing essential protection.
Managing Your Online Activity: Best Practices
Managing your online activity requires proactive control over privacy settings on platforms like Facebook, Instagram, and Twitter to safeguard personal information. Regularly reviewing and deleting old posts minimizes digital footprints and reduces the risk of data misuse. Employing strong passwords and two-factor authentication enhances account security, ensuring safer social media interactions.
Enhancing Privacy: Essential Configuration Tips
Enhancing privacy on social media platforms requires adjusting settings to limit data visibility, such as enabling two-factor authentication and restricting profile access to trusted contacts. Users should regularly review app permissions and deactivate location sharing to minimize personal information exposure. Customizing privacy controls ensures better protection against unauthorized data collection and enhances overall account security.
Which Tool Should You Use? Decision Guide
Choosing the right social media management tool depends on your business goals, budget, and platform preferences. Tools like Hootsuite excel in scheduling and analytics across multiple networks, while Buffer offers user-friendly interfaces ideal for small businesses. For advanced audience insights and real-time engagement, Sprout Social provides comprehensive solutions tailored to data-driven marketing strategies.
Keeping Your Data Safe: Final Recommendations
To keep your data safe on social media, regularly update privacy settings to control who can access your information and limit data sharing with third-party apps. Use strong, unique passwords combined with two-factor authentication to protect your accounts from unauthorized access. Be cautious about the personal information you share publicly and review access permissions frequently to minimize security risks.
 socmedb.com
socmedb.com