Photo illustration: WhatsApp Two-step verification vs Email verification
WhatsApp Two-step verification provides enhanced security by requiring a PIN during login, while email verification relies solely on access to the registered email account for identity confirmation. Explore the detailed comparison and security implications of both methods in this article.
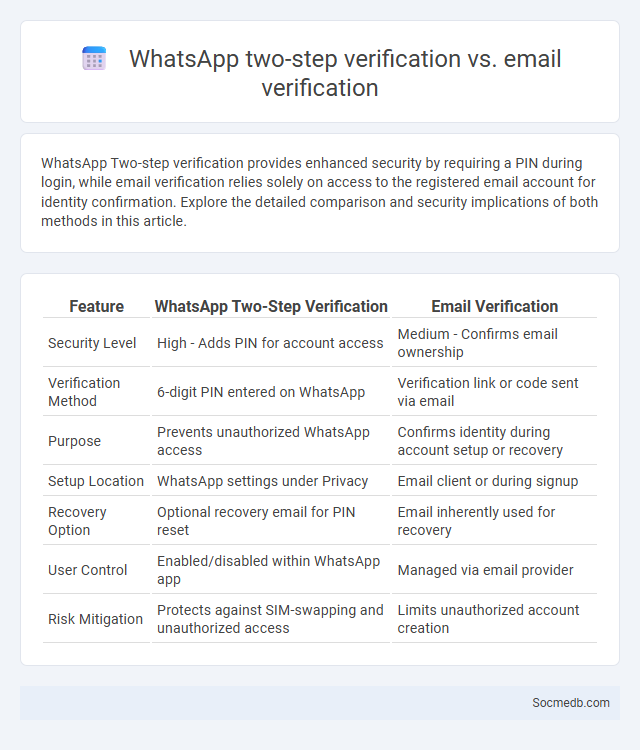
Table of Comparison
| Feature | WhatsApp Two-Step Verification | Email Verification |
|---|---|---|
| Security Level | High - Adds PIN for account access | Medium - Confirms email ownership |
| Verification Method | 6-digit PIN entered on WhatsApp | Verification link or code sent via email |
| Purpose | Prevents unauthorized WhatsApp access | Confirms identity during account setup or recovery |
| Setup Location | WhatsApp settings under Privacy | Email client or during signup |
| Recovery Option | Optional recovery email for PIN reset | Email inherently used for recovery |
| User Control | Enabled/disabled within WhatsApp app | Managed via email provider |
| Risk Mitigation | Protects against SIM-swapping and unauthorized access | Limits unauthorized account creation |
Introduction to Account Security Methods
Account security methods on social media platforms include multi-factor authentication, strong password creation, and regular privacy setting reviews. Enabling biometric login, such as fingerprint or facial recognition, enhances protection against unauthorized access. Users should stay vigilant about suspicious activity alerts and promptly update recovery information to maintain account integrity.
What is WhatsApp Two-Step Verification?
WhatsApp Two-Step Verification enhances your account security by requiring a six-digit PIN in addition to your phone number verification, protecting against unauthorized access. This feature helps safeguard your personal messages and data, especially if your SIM card is lost or stolen. You can enable Two-Step Verification within WhatsApp's security settings to add an extra layer of protection to your account.
How Email Verification Works
Email verification works by confirming the authenticity of an email address through a multi-step process involving syntax checking, domain validation, and mailbox existence confirmation. Syntax checking ensures the email follows proper formatting rules, while domain validation uses DNS records to verify the domain's validity and mail server availability. The final step, mailbox existence confirmation, often employs SMTP commands to check if the specific inbox is active without sending an actual email, significantly reducing bounce rates and enhancing communication reliability.
What is Standard Two-Step Verification?
Standard Two-Step Verification is a security process that requires users to provide two forms of identification before accessing their social media accounts. This typically involves entering a password followed by a one-time code sent via SMS, authentication apps, or email. Implementing this method significantly reduces the risk of unauthorized access and protects personal data from cyber threats.
Comparing Security Levels
Social media platforms vary significantly in security levels, with Facebook and Instagram implementing advanced encryption and multi-factor authentication to protect user data. Twitter emphasizes account protection through real-time monitoring of suspicious activities, while TikTok faces scrutiny for privacy concerns due to data sharing practices. LinkedIn offers enhanced security measures targeted at professional interactions, including strict access controls and regular security audits.
User Experience and Convenience
Social media platforms prioritize user experience and convenience by offering intuitive interfaces and personalized content feeds that keep you engaged. Seamless navigation, fast loading times, and integrated communication tools enhance interaction and accessibility across devices. These features collectively ensure your online social interactions are efficient, enjoyable, and tailored to your preferences.
Recovery Options and Potential Issues
Social media platforms offer various recovery options such as two-factor authentication, password reset links, and account recovery through verified email or phone numbers to secure user access. Potential issues include account hacking, identity theft, and temporary or permanent suspension due to policy violations or suspicious activities. Users should regularly update recovery information and monitor account activity to mitigate security risks effectively.
Vulnerabilities and Risks
Social media platforms expose users to significant vulnerabilities including identity theft, cyberbullying, and privacy breaches that compromise personal information. Data breaches and phishing attacks exploit weak security protocols, increasing the risk of unauthorized access to sensitive data. Users face psychological risks from misinformation, social engineering, and persistent online harassment that impact mental health and societal trust.
Best Practices for Enhanced Security
Implement strong, unique passwords and enable two-factor authentication across all social media accounts to prevent unauthorized access. Regularly update privacy settings to control who can view personal information and limit data sharing with third-party apps. Monitor account activity for suspicious behavior and promptly report any security breaches to the platform's support team.
Which Verification Method Should You Choose?
Choosing the right social media verification method depends on your platform and goals; account verification badges on Instagram, Twitter, and Facebook enhance credibility and visibility. Two-factor authentication (2FA) offers robust security, protecting your personal or business accounts from unauthorized access. Prioritize verification options that align with your needs to safeguard Your presence and build trust with your audience.
 socmedb.com
socmedb.com