Photo illustration: Authenticator App vs Security Key
Authenticator apps generate time-sensitive codes for two-factor authentication, providing convenient and secure access to accounts. Security keys use physical hardware for enhanced protection against phishing attacks. Discover the detailed advantages of each method in this article.
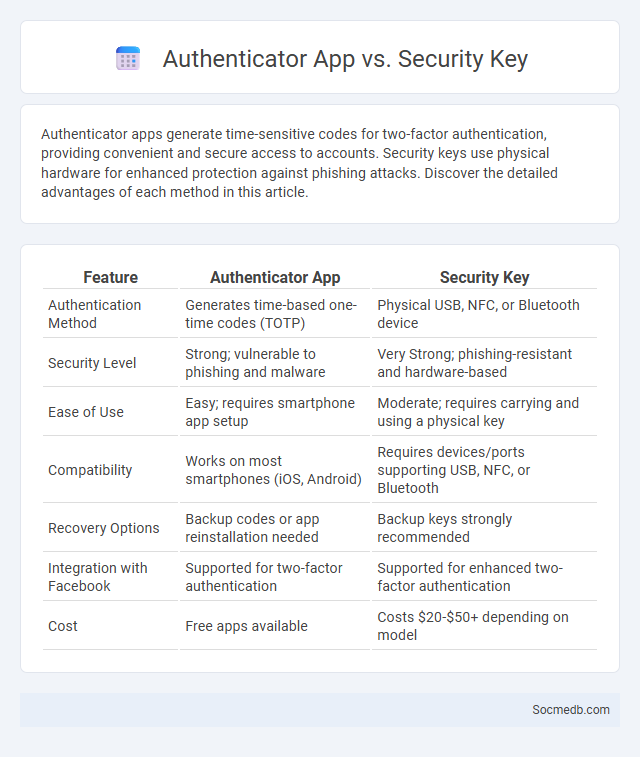
Table of Comparison
| Feature | Authenticator App | Security Key |
|---|---|---|
| Authentication Method | Generates time-based one-time codes (TOTP) | Physical USB, NFC, or Bluetooth device |
| Security Level | Strong; vulnerable to phishing and malware | Very Strong; phishing-resistant and hardware-based |
| Ease of Use | Easy; requires smartphone app setup | Moderate; requires carrying and using a physical key |
| Compatibility | Works on most smartphones (iOS, Android) | Requires devices/ports supporting USB, NFC, or Bluetooth |
| Recovery Options | Backup codes or app reinstallation needed | Backup keys strongly recommended |
| Integration with Facebook | Supported for two-factor authentication | Supported for enhanced two-factor authentication |
| Cost | Free apps available | Costs $20-$50+ depending on model |
Introduction to Digital Authentication Methods
Digital authentication methods on social media platforms include multi-factor authentication (MFA), biometric verification, and OAuth protocols to enhance user security. These techniques ensure that users' identities are verified through multiple layers, reducing the risk of unauthorized access and identity theft. Implementing advanced authentication frameworks protects both personal data and platform integrity against cyber threats.
What is Two-Factor Authentication (2FA)?
Two-Factor Authentication (2FA) enhances social media security by requiring two forms of verification before granting access to your account. Typically, it combines something you know, like a password, with something you have, such as a smartphone-generated code or authentication app. Implementing 2FA significantly reduces the risk of unauthorized access, protecting your personal data and online presence from hackers.
Understanding Authenticator Apps
Authenticator apps generate time-based, one-time passcodes (TOTPs) to enhance your account security by requiring a second verification step during login. These apps, such as Google Authenticator or Microsoft Authenticator, sync with your accounts using QR codes to provide dynamic codes that change every 30 seconds, preventing unauthorized access. By integrating authenticator apps into your social media accounts, you significantly reduce the risk of hacking and protect your personal information from cyber threats.
Security Keys Explained
Security keys are physical devices used to enhance social media account protection by providing two-factor authentication (2FA). These keys generate unique cryptographic codes, preventing unauthorized access even if passwords are compromised. Platforms like Facebook, Twitter, and Instagram support security keys to ensure stronger, phishing-resistant login security.
Key Differences: Authenticator App vs Security Key vs 2FA
Authenticator apps generate time-based one-time passwords (TOTPs) that enhance your social media account security by requiring a temporary code after your password. Security keys use physical hardware devices, such as USB or NFC tokens, to provide phishing-resistant authentication, offering a higher security level compared to app-generated codes. Two-factor authentication (2FA) combines something you know (password) with something you have (authenticator app or security key) to significantly reduce unauthorized access on social platforms.
Security Strength Comparison
Social media platforms vary significantly in their security strength, with some offering end-to-end encryption, two-factor authentication, and advanced privacy controls, while others have weaker protections leading to potential data breaches. Your account's vulnerability largely depends on the platform's commitment to security protocols and responsiveness to emerging cyber threats. Choosing a social media service with robust encryption standards and proactive security measures ensures better protection of your personal information.
Usability and User Experience
Social media platforms prioritize intuitive navigation and personalized content to enhance usability, ensuring users can effortlessly connect and share information. Optimized interface design reduces cognitive load, increasing engagement and session duration. Continuous user feedback integration drives improvements in accessibility and overall user experience across diverse demographics.
Compatibility and Platform Support
Social media platforms vary widely in compatibility across devices, ensuring Your access on smartphones, tablets, and desktops without performance loss. Leading networks like Facebook, Instagram, and Twitter offer dedicated apps optimized for iOS and Android, enhancing user experience through seamless interaction and fast loading times. Cross-platform support extends to web browsers like Chrome, Safari, and Firefox, guaranteeing that Your content remains accessible regardless of operating system or device type.
Choosing the Best Authentication Solution
Choosing the best authentication solution for social media platforms ensures robust security against unauthorized access and data breaches. Implementing multi-factor authentication (MFA) or biometric verification significantly enhances user account protection by requiring multiple forms of identity confirmation. To safeguard Your social media presence, prioritize authentication methods that balance strong security features with user convenience and seamless integration.
Conclusion: Which Authentication Method is Right for You?
Choosing the right authentication method for your social media accounts depends on balancing security and convenience. Two-factor authentication (2FA) offers enhanced protection by requiring multiple verification steps, reducing the risk of unauthorized access. Evaluate your threat level and usage habits to decide whether SMS codes, authenticator apps, or biometric options best secure your online presence.
 socmedb.com
socmedb.com