Photo illustration: Twitter vs Tumblr ban evasion
Twitter implements advanced algorithms and real-time monitoring to detect and block ban evasion efforts, whereas Tumblr relies more on community reporting and manual moderation to curb similar violations. Explore this article to understand the differing strategies and effectiveness of ban evasion prevention on these platforms.
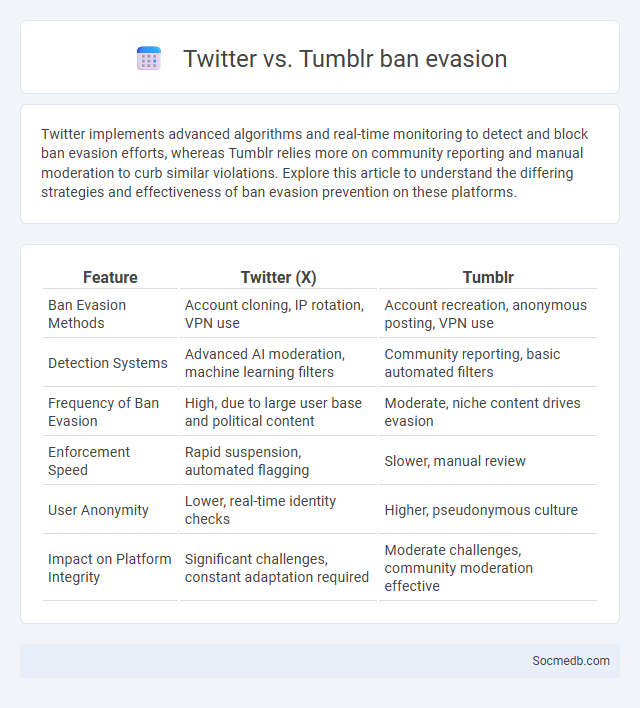
Table of Comparison
| Feature | Twitter (X) | Tumblr |
|---|---|---|
| Ban Evasion Methods | Account cloning, IP rotation, VPN use | Account recreation, anonymous posting, VPN use |
| Detection Systems | Advanced AI moderation, machine learning filters | Community reporting, basic automated filters |
| Frequency of Ban Evasion | High, due to large user base and political content | Moderate, niche content drives evasion |
| Enforcement Speed | Rapid suspension, automated flagging | Slower, manual review |
| User Anonymity | Lower, real-time identity checks | Higher, pseudonymous culture |
| Impact on Platform Integrity | Significant challenges, constant adaptation required | Moderate challenges, community moderation effective |
Understanding Ban Evasion: Definitions and Context
Ban evasion on social media refers to the act of circumventing restrictions or suspensions imposed by a platform by creating new accounts or using alternative methods to regain access. Understanding ban evasion is critical for maintaining community standards and ensuring that users adhere to platform policies. Your awareness of these tactics helps in recognizing violations and fostering a safer online environment.
Twitter’s Policies on Ban Evasion
Twitter's policies on ban evasion strictly prohibit users from creating new accounts to circumvent suspensions or bans, emphasizing the platform's commitment to maintaining a safe community. Enforcement actions include permanent suspension of both the original and any evasion accounts detected through behavioral analysis and IP tracking. Protecting Your account and adhering to Twitter's rules is crucial to avoid penalties and ensure continued access to the platform's services.
Tumblr’s Approach to Ban Evasion
Tumblr employs advanced algorithms and machine learning to detect and prevent ban evasion by users attempting to circumvent suspension or content restrictions. The platform continuously updates its terms of service and moderation tools to identify alternate accounts and repeated violations, protecting the community from harmful or disruptive behavior. Your account safety depends on Tumblr's proactive measures to maintain a secure and compliant social media environment.
Key Differences: Twitter vs. Tumblr Ban Evasion
Twitter relies on real-time updates and brief text posts, making its ban evasion techniques heavily dependent on quickly created alternative accounts and proxy IP addresses. Tumblr's ban evasion strategies focus more on content re-hosting and anonymous blog creation due to its emphasis on multimedia and longer-form posts. Twitter's API restrictions and rigorous account verification create more technical barriers compared to Tumblr's more permissive, community-driven platform structure.
Detection Techniques Used by Both Platforms
Social media platforms employ advanced detection techniques such as machine learning algorithms, natural language processing, and image recognition to identify harmful content and policy violations. These systems continuously analyze user behavior patterns, flagged posts, and metadata to ensure a safer online environment for Your interactions. Real-time monitoring combined with automated classification tools enables both platforms to efficiently detect and mitigate spam, misinformation, and malicious activities.
User Strategies for Ban Evasion on Twitter
Users employing ban evasion strategies on Twitter often create alternate accounts by varying usernames, adopting VPNs, or using different devices to circumvent platform restrictions. Many tactics involve mimicking original content styles while avoiding direct policy violations to maintain follower engagement and avoid detection by Twitter's automated systems. Your success in navigating these methods depends on staying informed about Twitter's evolving moderation algorithms and maintaining consistent user behavior patterns.
Common Ban Evasion Methods on Tumblr
Common ban evasion methods on Tumblr include creating multiple alternate accounts, using VPNs or proxies to mask IP addresses, and frequently changing usernames or blog URLs to avoid detection. Users often exploit these tactics to bypass platform restrictions and continue posting prohibited content, undermining community guidelines. Protecting your account requires awareness of these evasion techniques and reporting suspicious activity to maintain a safe online environment.
Consequences of Ban Evasion: Platform Actions
Social media platforms employ advanced detection algorithms to identify and restrict users engaging in ban evasion, resulting in account suspension or permanent removal. You may face loss of community access and content deletion as platforms enforce strict policies to maintain user safety and platform integrity. Repeated violations often trigger escalated enforcement measures, including IP blocking and device bans to prevent further evasion attempts.
Ethical and Legal Implications of Ban Evasion
Engaging in social media ban evasion raises significant ethical concerns by undermining platform regulations designed to protect user safety and community standards. Legal implications may include violations of terms of service that could lead to account suspension, civil penalties, or even criminal charges under laws targeting identity fraud and cybercrime. Your awareness of these consequences is crucial to maintaining responsible digital behavior and avoiding potential legal troubles.
Future Trends in Combating Ban Evasion on Social Media
Future trends in combating ban evasion on social media include leveraging advanced AI algorithms and machine learning to detect and block users creating multiple accounts. Behavioral biometrics and cross-platform identity verification are increasingly utilized to identify evasion tactics in real time. Emerging technologies such as decentralized identity frameworks and blockchain-based verification aim to enhance security and accountability, reducing the risk of repeat offenses.
 socmedb.com
socmedb.com