Photo illustration: WhatsApp vs Zoom encryption
WhatsApp employs end-to-end encryption for all messages and calls by default, ensuring only participants can access the content, while Zoom uses AES 256-bit encryption but offers end-to-end encryption as an optional feature requiring special configuration. Discover detailed differences and security implications of WhatsApp vs Zoom encryption in this article.
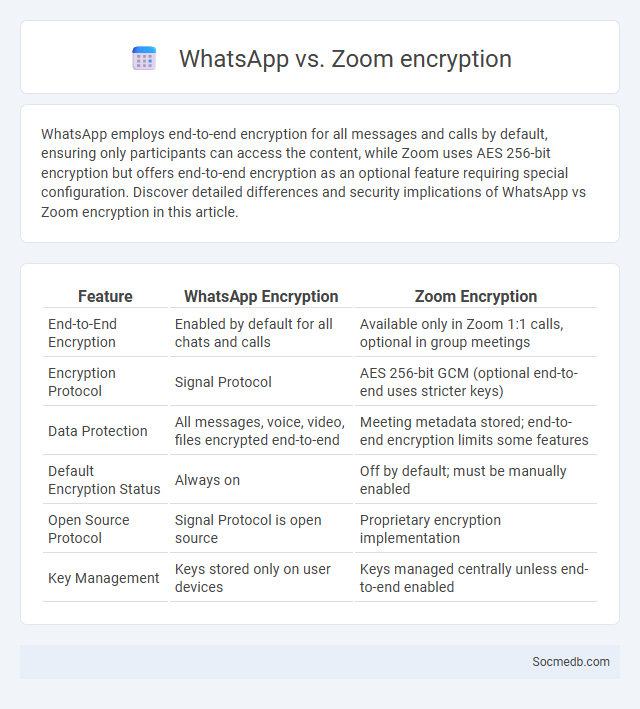
Table of Comparison
| Feature | WhatsApp Encryption | Zoom Encryption |
|---|---|---|
| End-to-End Encryption | Enabled by default for all chats and calls | Available only in Zoom 1:1 calls, optional in group meetings |
| Encryption Protocol | Signal Protocol | AES 256-bit GCM (optional end-to-end uses stricter keys) |
| Data Protection | All messages, voice, video, files encrypted end-to-end | Meeting metadata stored; end-to-end encryption limits some features |
| Default Encryption Status | Always on | Off by default; must be manually enabled |
| Open Source Protocol | Signal Protocol is open source | Proprietary encryption implementation |
| Key Management | Keys stored only on user devices | Keys managed centrally unless end-to-end enabled |
Introduction to Messaging and Video Call Encryption
Messaging and video call encryption ensures that communications on social media platforms are protected from unauthorized access by converting messages and video data into secure, unreadable codes. End-to-end encryption (E2EE) is the most common method, guaranteeing that only the sender and recipient can decode the content, preventing interception by hackers or service providers. This technology enhances user privacy, builds trust in social media applications, and complies with growing data protection regulations worldwide.
Overview: WhatsApp Encryption Features
WhatsApp employs end-to-end encryption to secure all messages, calls, photos, and videos shared on its platform, ensuring that only you and the recipient can access the content. This encryption uses the Signal Protocol, which provides a robust layer of security by generating unique lock and key pairs for each message. Privacy features also include encrypted group chats and secure backup options, safeguarding your communications from interception or unauthorized access.
Zoom Encryption Protocols Explained
Zoom employs advanced encryption protocols to safeguard user communications, utilizing AES 256-bit GCM encryption for in-meeting data and RSA 2048-bit encryption for key exchange and authentication. This robust security framework ensures the confidentiality and integrity of voice, video, and chat data during virtual meetings. By implementing end-to-end encryption options, Zoom enhances privacy by securing communications from unauthorized access, meeting the stringent standards required for enterprise and personal use.
What Is End-to-End Encryption (E2EE)?
End-to-End Encryption (E2EE) is a security protocol that ensures only the communicating users can read the messages, preventing third parties from accessing the data. It encrypts the message on the sender's device and only decrypts it on the recipient's device, making platforms like WhatsApp and Signal popular for secure social media messaging. This encryption method protects user privacy by safeguarding conversations from hackers, service providers, and governments.
How WhatsApp Implements End-to-End Encryption
WhatsApp implements end-to-end encryption using the Signal Protocol, which ensures that only you and the recipient can read the messages by encrypting them on the sender's device and decrypting only on the receiver's device. This encryption protects text, voice messages, calls, photos, and videos from interception by third parties, including WhatsApp itself. Your privacy is maintained through unique encryption keys stored solely on your device, making unauthorized access virtually impossible.
Zoom’s Approach to End-to-End Encryption
Zoom implements end-to-end encryption (E2EE) to enhance user privacy during virtual meetings by encrypting data directly on participants' devices, preventing unauthorized access including from Zoom servers. This approach utilizes a robust key management system where encryption keys are generated and managed on user devices, ensuring that only the intended recipients can decrypt meeting content. Zoom's E2EE supports up to 200 participants and requires users to enable this feature per meeting, balancing security with feature accessibility.
Security Differences: WhatsApp vs Zoom
WhatsApp encrypts all messages by default using end-to-end encryption, ensuring your conversations remain private between you and the recipient, while Zoom offers optional end-to-end encryption that must be enabled by users. WhatsApp's encryption extends to calls, messages, photos, and videos, whereas Zoom primarily focuses on securing video calls and meetings with broader controls for hosts. By understanding these security differences, you can make informed decisions about which platform best protects your sensitive communication.
Privacy Implications: User Data Protection
Social media platforms collect vast amounts of personal information, raising significant privacy implications for users worldwide. Ensuring robust data protection involves implementing encryption, strict access controls, and transparent privacy policies that clearly outline data usage. You must regularly review and adjust your privacy settings to safeguard your personal information from unauthorized access and misuse.
Common Misconceptions About E2EE
End-to-end encryption (E2EE) is often misunderstood as making messages completely invulnerable to interception, but it primarily ensures that only the communicating users can read the messages, not the service providers. Many believe E2EE guarantees anonymity, yet it does not hide metadata such as who is communicating and when. Users frequently overlook that E2EE cannot protect against device-level compromises, meaning if an endpoint is infected with malware, encrypted messages can still be exposed.
Choosing the Right App: Encryption and Privacy Factors
Choosing the right social media app requires careful consideration of encryption protocols and privacy policies to protect your personal data. End-to-end encryption ensures that only you and the intended recipient can access your messages, preventing unauthorized surveillance. Prioritizing apps with transparent data handling and strong user privacy settings enhances your overall online security.
 socmedb.com
socmedb.com